ISO 27701 is a widely adopted standard for managing privacy information, and risk assessment is a crucial component of its privacy management framework. ISO 27701 requires organizations to conduct regular risk assessments to identify potential privacy breaches and implement appropriate controls to mitigate the risks. This involves identifying, evaluating, and prioritizing privacy risks for the organization and its stakeholders. Risk assessment helps organizations identify the PII they collect, process, store, and share and assess the likelihood and impact of privacy breaches.
In this article, we will take a closer look at the ISO 27701 risk assessment process, including its key steps, methodologies, and tools. We will also discuss how risk assessment can help organizations to comply with privacy regulations, reduce the likelihood and impact of privacy breaches, and enhance customer trust and confidence.
What is ISO 27701?
A Privacy Information Management System (PIMS) should be established, implemented, maintained, and constantly improved in conformity with the General Data Protection Regulation (GDPR), according to ISO 27701, a privacy management standard. The International Organization for Standardization (ISO) created the standard to assist enterprises in safeguarding personal data and adhering to the GDPR’s privacy requirements.
In order to particularly address privacy management, ISO 27701 expands the framework of ISO 27001, a well-known standard for information security management systems. It offers a thorough method for managing privacy, including rules for data protection, risk analysis, continual observation and assessment, and the constant development of privacy management procedures. The ISO 27701 management system may be linked with current management systems, including ISO 27001, and is intended to be adaptable to enterprises of all sizes and sectors.
Organizations may show their dedication to privacy, comply with legal obligations, enhance their overall privacy policies, and gain the trust of their stakeholders and consumers by embracing ISO 27701.
Related Links
ISO 27001 Certification
ISO 20000 Certification
ISO 22301 Certification
ISO 21001 Certification
ISO 41001 Certification
ISO 50001 Certification
ISO 29001 Certification
ISO 14001 Certification
ISO 45001 Certification
ISO 22000 Certification
ISO 17025 Certification
ISO 13485 Certification
WHO SHOULD COMPLY WITH ISO 27701?
Any organization that processes personal data is subject to ISO 27701, which aims to create, implement, maintain, and continuously enhance a Privacy Information Management System (PIMS) in compliance with the General Data Protection Regulation (GDPR).
Organizations that are subject to GDPR, such as those situated in the European Union (EU) or those that handle the personal data of EU citizens, should pay particular attention to ISO 27701. Any organization that processes personal data and wishes to demonstrate its dedication to privacy management and compliance with privacy laws may, however, adopt the standard.
Companies of all sizes and in all sectors, including those in the public and commercial sectors, non-profits, and governmental bodies, can use ISO 27701. To simplify compliance efforts and lighten the administrative load, the standard can be linked with already-in-use management systems, such as ISO 27001.
HOW DOES ISO 27701 HELP ORGANIZATIONS?
According to the guidelines of the General Data Protection Regulation (GDPR), ISO 27701 offers businesses a framework for creating, implementing, maintaining, and continuously improving a privacy information management system (PIMS). Organizations can gain from implementing ISO 27701 in a number of ways:
Demonstrating compliance: Providing a thorough framework for privacy management, ISO 27701 assists organizations in demonstrating compliance with the GDPR and other privacy laws. According to the guideline, businesses must have safeguards in place to secure customer information, including risk analyses, data protection procedures, and employee privacy training.
Building trust: Companies may increase trust among their stakeholders and consumers by showcasing their dedication to privacy management. ISO 27701 provides a framework for fostering a privacy culture within an organization and encouraging transparency in privacy practices.
Improving data protection: In order to safeguard personal data from unlawful access, use, or disclosure, ISO 27701 mandates that businesses employ data protection procedures such as encryption and access restrictions. Organizations may enhance their data protection procedures and lower the risk of data breaches by putting these policies in place.
Increasing commercial opportunities: By showcasing an organization’s dedication to privacy and adherence to privacy laws, ISO 27701 can give it a competitive edge. Increased business opportunities may result from this, such as joint ventures with other institutions that place a high value on privacy management.
Streamlining compliance: Compliance activities may be made more efficient, and the administrative load associated with handling various compliance standards can be decreased by integrating ISO 27701 with current management systems, such as ISO 27001.
ROLE OF RISK ASSESSMENT IN ISO 27701
Performing risk assessments is essential for conforming to ISO 27701. Organizations can identify possible privacy issues related to the processing of personal data and implement suitable countermeasures by conducting a thorough risk assessment. An integral part of the Privacy Information Management System (PIMS) created in accordance with ISO 27701 is the risk assessment process. In order to manage the privacy of personal data across the whole data lifecycle, from collection to disposal, companies can use the PIMS. At each stage of the data lifecycle, the risk assessment process is used to detect possible privacy issues, such as those connected to illegal access, processing mistakes, and data breaches. Organizations are required by ISO 27701 to undertake a thorough risk assessment that considers the possibility and consequences of privacy issues as well as the efficacy of current safeguards.
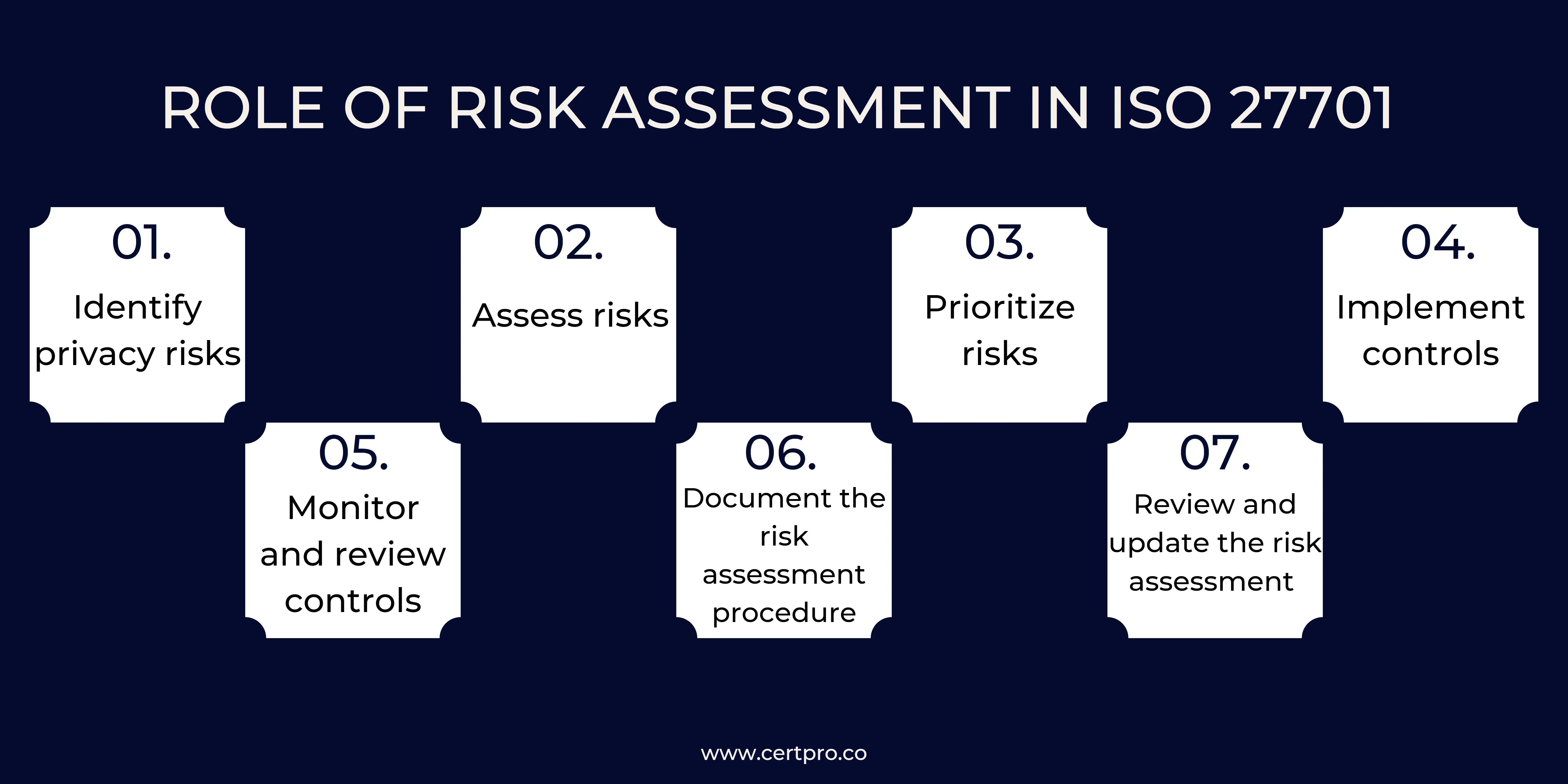
Following are some key procedures for conducting an exhaustive risk assessment that complies with ISO 27701:
1. Identify privacy risks: identifying possible privacy hazards to the organization’s information assets is the first step in completing a risk assessment. This could include dangers related to handling personal data, like unauthorized access or disclosure, security lapses, or failure to adhere to data protection laws.
2. Assess risks: The company must evaluate the possibility and effect of possible privacy threats when they are discovered. This may entail assessing the likelihood of a risk occurring and its possible effects on the organization using tools and techniques for risk analysis, such as threat modeling.
3. Prioritize risks: After evaluating privacy threats, the organization should prioritize risk management initiatives by allocating resources to the most significant risks and assessing the risks based on their likelihood and impact.
4. Implement controls: The company must put the best controls in place to manage the risks it has identified and prioritized as being the most important. To lessen the possibility and effect of a risk occurring, this may entail installing technological and organizational safeguards like access restrictions, encryption, or data reduction.
5. Monitor and review controls: Controls should be evaluated and revised often in order to ensure their efficacy in reducing privacy threats. This will ensure that the measures are compliant with legal standards and continue to be effective in lowering privacy concerns.
6. Document the risk assessment procedure: It is crucial to keep track of the steps taken to mitigate privacy concerns during the risk assessment procedure. Build confidence with consumers and stakeholders by using this paperwork to show compliance with ISO 27701 and other privacy laws.
7. Review and update the risk assessment frequently: To keep the risk assessment current and useful throughout time, it is crucial to do so frequently. This can be carried out either routinely or if there are major changes to the organization’s privacy threats or operational setting.
The importance of risk assessment in attaining ISO 27701 compliance cannot be overstated. A thorough risk assessment assists companies in identifying possible privacy concerns connected to the processing of personal data and in putting in place the necessary safeguards to reduce such risks. Organizations may lower the risk of data breaches and other privacy events by giving privacy management activities top priority while also demonstrating compliance with privacy laws.
Stay ISO 27701 compliant with the help of CertPro
As a trustworthy certification supplier, CertPro provides helpful insight and direction throughout the ISO 27701 compliance process. Their team of skilled specialists can help businesses undertake thorough risk analyses that are adapted to their particular privacy demands and legal requirements. They provide their expertise in the field and best practices to assist firms in identifying and prioritizing privacy issues, putting in place the necessary safeguards, and creating robust risk management plans.
Additionally, CertPro’s certification services offer unbiased confirmation of a company’s adherence to ISO 27701. Organizations that work with CertPro may be sure that their privacy management procedures adhere to international standards and show a commitment to safeguarding personal data.
FAQ
What function does risk assessment serve in ensuring ISO 27701 compliance?
What are the key procedures for conducting an exhaustive risk assessment that complies with ISO 27701?
How can businesses improve the way they conduct risk assessments to guarantee ISO 27701 compliance?
program, organizations can improve their risk assessment processes.
What are the primary concepts of ISO/IEC 27701?
What does "ISO 27701 certified" refer to?

About the Author
NICOLENE KRUGER
Nicolene Kruger, Regional Manager in South Africa, is an experienced Legal Counsel with expertise in compliance and auditing. Her strategic, solution-driven approach aligns legal standards with business objectives, ensuring seamless adherence to regulations.
COMPLIANCE RISK MANAGEMENT: EXPERT STRATEGIES AND BEST PRACTICES
Compliance risk considers the organization's potential legal, material, and financial losses due to compliance failure. Thus, compliance risk is known as integrity risk. Organizations of all sizes are exposed to compliance risk. Hence, compliance failure results in...
TOP 7 DATA LOSS PREVENTION STRATEGIES IN 2024
In the contemporary business landscape, data is the cornerstone of organizational vitality. Businesses leverage data extensively to inform decisions, maintain competitiveness, and foster expansion. Nonetheless, they encounter multifaceted challenges emanating from...
TIPS FOR ARTICULATING YOUR SECURITY POSTURE TO STAKEHOLDERS
Cybersecurity is now a top-tier priority for any Organization. Data breaches can ruin the entire company, destroy customer trust, and damage reputation. However, companies can find decision-making difficulties because stakeholders, board members, department heads, and...




