SOC 2
Service Organization ControlS
SOC 2 (Service Organization Controls) certification plays a vital role in assessing an organization’s system and organization controls, encompassing security, availability, processing integrity, confidentiality, and privacy. SOC 2 holds significant importance in ensuring the integrity and security of an organization’s data and mitigating risks associated with outsourcing critical operations.
In today’s digital world, where data breaches and cyber threats are rampant, SOC 2 certification is becoming increasingly important, particularly for organizations operating within software-as-a-service (SaaS) environments. SOC 2 for SaaS providers ensures that they adhere to rigorous standards, employ robust security measures, and safeguard client data, enabling organizations to embrace cloud-based solutions.
SOC 2 certification offers numerous benefits for organizations, including establishing trust, meeting regulatory requirements, mitigating risks, safeguarding against data breaches, and enhancing overall security. It assures clients that their sensitive data is in safe hands, enabling organizations to attract and retain clients while maintaining the integrity and confidentiality of their data.

Certification and Auditing Services by CertPro For SOC 2 Certification
SOC 2 certification is crucial for organizations aiming to demonstrate their commitment to data security, privacy, and operational excellence. At CertPro, we understand the significance of SOC 2 certification and offer comprehensive support to organizations seeking to achieve this milestone. Our team of experienced professionals will guide you through the entire SOC 2 certification process, ensuring that your organization’s systems, processes, and controls meet the rigorous requirements set forth by the American Institute of CPAs (AICPA).
Why choose CertPro for SOC 2 certification and auditing?
When it comes to SOC 2 certification and auditing, CertPro stands out as a trusted and experienced provider. Our extensive knowledge of SOC 2 requirements and proven track record make us the ideal choice for organizations striving to demonstrate their commitment to data security, privacy, and operational excellence. Here’s why you should choose CertPro for your SOC 2 certification needs:
| Factors | CertPro Advantage |
|---|---|
| Time to Certification | 4x faster than traditional approaches |
| Price | Competitive rates with flexible options |
| Process | Streamlined and efficient methodology |
| Expertise | 10+ years of industry experience |
Certpro’s Cost-Effective Approach to SOC 2 Certification
When organizations consider SOC 2 certification, the total SOC 2 cost can sometimes be a concern, considering the various factors that contribute to overall expenses. At CertPro, we understand the importance of cost-effectiveness and offer a tailored pricing structure for SOC 2 certification based on your organization’s specific needs. Our transparent pricing model allows you to easily determine the SOC 2 cost associated with achieving SOC 2 compliance. Here’s an overview of our pricing:
| No. of employees | Timeline | Cost (approx.) |
| 1 – 25 | 6 weeks | 4750 USD |
| 25-100 | 8 weeks | 6750 USD |
| 100-250 | 8-10 weeks | 9750 USD |
| 250 plus | 12 weeks | Custom plans |
| For SOC 2 Type II audit attestation post Type I @ 3000 USD |
UNDERSTANDING SOC 2
The American Institute of Certified Public Accountants (AICPA) established SOC 2 (Service Organization Control 2), a widely used auditing standard. It focuses on the system and organization controls for service providers that store, process, or transmit sensitive data. SOC 2 reports provide detailed information about the effectiveness of these controls in ensuring security, availability, processing integrity, confidentiality, and privacy.
The SOC (Service Organization Control) suite of services consists of SOC 1, & SOC 2. These services are designed to provide assurance and confidence to clients and stakeholders regarding an organization’s controls and practices.
- SOC 1: SOC 1 reports, also known as SSAE 18 reports, focus on the controls related to financial reporting. They assess the effectiveness of an organization’s internal controls over financial reporting and are typically relevant for companies providing outsourced services that impact their clients’ financial statements.
- SOC 2: SOC 2 report evaluates an organization’s controls for security, availability, processing integrity, confidentiality, and privacy, assuring the effectiveness of their systems and organization control measures. It assesses the system and organization controls on financial reporting and is commonly used for SaaS providers, cloud service providers, and other technology-related companies to demonstrate their commitment to data security.
These SOC reports and services are essential for organizations to demonstrate their commitment to security, privacy, financial controls, cybersecurity, and supply chain integrity. They provide valuable information to clients, stakeholders, and regulatory bodies, instilling confidence in the organization’s ability to protect sensitive data and meet relevant compliance requirements.
SOC for Cybersecurity and Supply Chain are two specialized assessments within the SOC framework that focus on specific areas of risk management.
- SOC for Cybersecurity: SOC for Cybersecurity is an evaluation specifically focused on an organization’s cybersecurity risk management program, providing an in-depth assessment of its effectiveness. It evaluates the effectiveness of controls and processes related to identifying, protecting against, detecting, responding to, and recovering from cybersecurity incidents
- SOC for Supply Chain: SOC for Supply Chain is a newer addition to the SOC suite. It addresses the risks associated with an organization’s supply chain and assesses the controls in place to manage those risks. The SOC for Supply Chain evaluates procurement, vendor management, logistics, and information security processes to verify the security and integrity of the supply chain.
SOCs for cybersecurity and supply chain integrity provide organizations with valuable insights and assurances regarding their risk management practices in critical areas, helping to establish trust, mitigate risks, and demonstrate a commitment to cybersecurity and supply chain integrity.
THE STEPS TO GET SOC 2 CERTIFICATION
SOC 2 certification involves several essential steps to ensure compliance with the necessary standards. While the specific process may vary depending on the organization and the chosen certification body, the general steps to obtain SOC 2 certification are as follows:
1. Understand the Scope: Determine the scope of your SOC 2 certification, including the systems and controls that need to be evaluated. Identify the relevant trust services categories (e.g., security, availability, processing integrity, confidentiality, and privacy) based on your organization’s specific needs.
2. Assess Current Controls: Conduct an internal assessment to evaluate your existing controls and identify gaps or areas that require improvement to meet SOC 2 compliance requirements. This step involves conducting a risk assessment and documenting policies and procedures.
3. Remediate Gaps: Address the gaps identified in the previous step by implementing necessary controls and enhancing existing processes. This may involve implementing security measures, enhancing data protection practices, and improving documentation and monitoring procedures.
4. Engage a CPA Firm: Select a Certified Public Accountant (CPA) firm with experience in SOC 2 audits to perform the examination. Engage in discussions with the firm to determine the scope, timeline, and cost of the audit.
5. Pre-Assessment Readiness Review: Conduct an internal readiness review to assess your preparedness for the SOC 2 audit. This involves ensuring that controls are properly implemented, evidence is readily available, and documentation is complete.
6. SOC 2 Audit: The CPA firm performs the formal SOC 2 examination, which includes testing the effectiveness of controls, reviewing documentation, conducting interviews, and verifying compliance with SOC 2 criteria.
7. Receive Audit Report: Upon completion of the audit, the CPA firm issues a SOC 2 report that includes the auditor’s opinion and details about the scope of the examination, control objectives, and the effectiveness of controls. There are two types of SOC 2 reports: Type I (point-in-time assessment) and Type II (assessment over a specified period).
8. Ongoing Compliance: Maintain ongoing compliance by continuously monitoring and evaluating your controls, conducting regular risk assessments, addressing any identified gaps or weaknesses, and performing periodic SOC 2 audits to demonstrate ongoing adherence to the standards.
It’s important to note that working with an experienced audit firm or consultant can assist in navigating the SOC 2 certification process, ensuring that all necessary steps are followed, and maximizing the chances of successful certification.

IMPORTANCE OF SOC 2
SOC 2 compliance is essential for protecting sensitive data and maintaining individuals’ privacy rights. Adherence to SOC 2 standards demonstrates an organization’s commitment to data security, which fosters trust among customers and stakeholders. SOC 2 compliance helps to meet regulatory standards, reduce risks associated with data breaches, and facilitate timely incident responses. Furthermore, it provides a competitive advantage by distinguishing compliant firms in the marketplace. SOC 2 encourages process improvement while also cultivating a culture of security and privacy awareness. Overall, SOC 2 is critical for data protection, compliance, and retaining customer and partner trust.
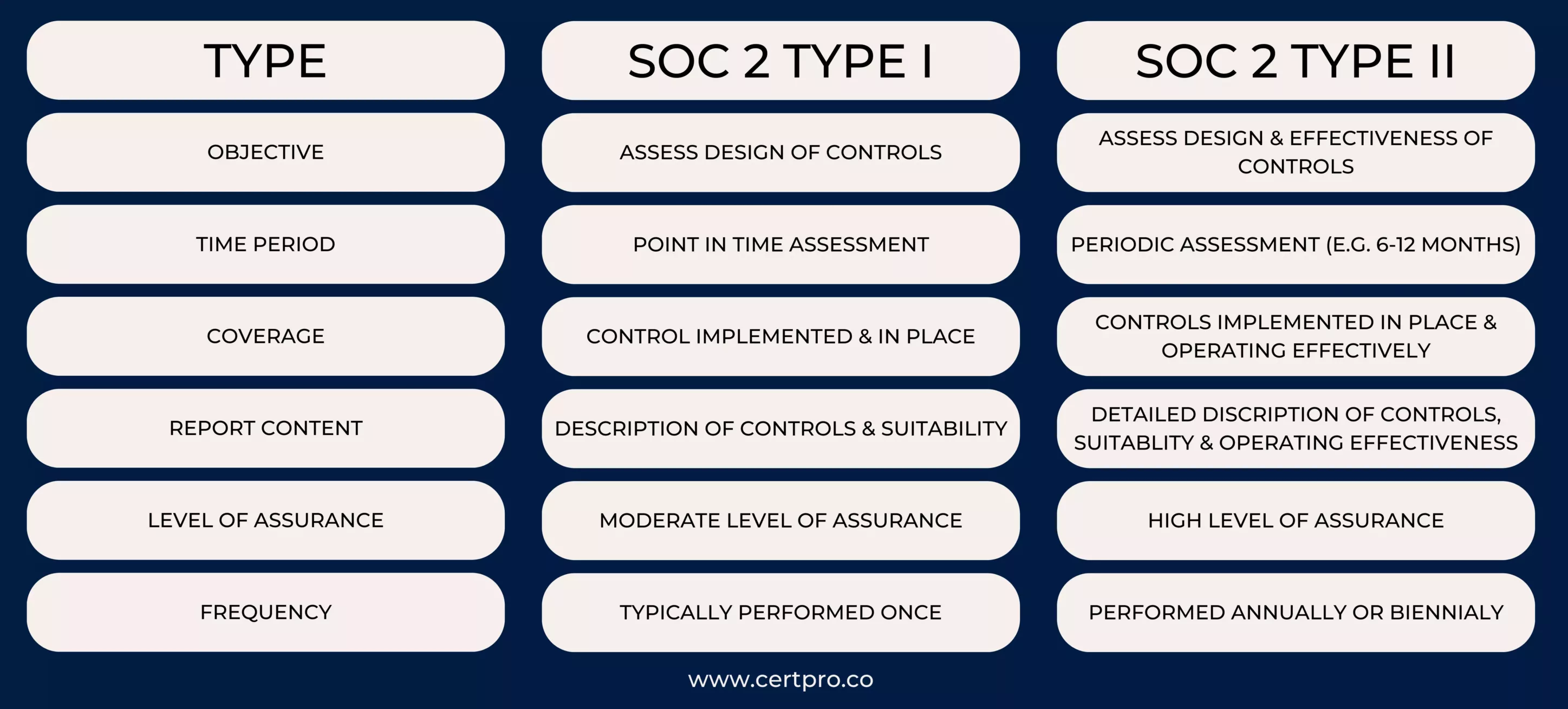
COMPARING SOC 2 EVALUATIONS: TYPE I VS TYPE II
SOC 2 audits come in two different types: Type I and Type II. The key difference between the two types lies in the duration and scope of the audit.
A GUIDE TO SOC 2 REPORTING
SOC 2 reporting uses processes like scoping, control selection, testing, and reporting to assess an organization’s security, processing integrity, confidentiality, availability, and privacy controls. There are two varieties: type I and type II, with different areas of concentration. SOC 2 accreditation requires a significant financial, time, and internal effort commitment, but it also provides advantages, including improving security, increasing customer trust, and earning competitive advantages. Organizations can navigate the certification process more successfully if they work with a skilled auditor and understand the expectations and standards for SOC 2 reporting. Organizations can enhance their competitiveness in the market and cultivate client trust by comprehending and adhering to these standards, which also show their dedication to data security and integrity.
A PRACTICAL APPROACH TO DIFFERENT SOC 2 COMPLIANCE TYPES
SOC 2 compliance comes in different types, each with its own objectives and requirements. A practical approach to different types of SOC 2 compliance involves the following steps:
- Type I Compliance: This type of SOC 2 compliance evaluates the suitability and design of an organization’s controls at a specific point in time. To achieve Type I compliance, organizations need to define the scope, understand the relevant Trust Services Criteria (TSC), identify risks, develop controls, and perform internal assessments.
- Type II Compliance: This type of SOC 2 compliance evaluates the operating effectiveness of an organization’s controls over a specified period, typically six to twelve months. To achieve Type II compliance, organizations need to follow the same steps as Type I but also implement the defined controls and engage external auditors to perform an independent audit.
By following this practical approach to different types of SOC 2 compliance, organizations can ensure they meet regulatory requirements, protect data, and demonstrate a commitment to data security and privacy to their stakeholders.
SOC 2 REQUIREMENTS: A COMPREHENSIVE OVERVIEW
SOC 2 requirements encompass a set of criteria that organizations must meet to achieve compliance with the SOC 2 framework. These requirements focus on evaluating an organization’s controls related to security, availability, processing integrity, confidentiality, and privacy. Here are some key requirements of SOC 2:
- Control Objectives: Organizations must define specific control objectives within each trust services category (TSC) applicable to their business. These objectives outline the desired outcomes that the controls aim to achieve to protect customer data and meet industry best practices.
- Written Policies & Procedures: Organizations need to establish written policies and procedures that detail the processes and protocols for managing and safeguarding sensitive data. These documents serve as a reference for employees and provide guidelines on how to handle data securely.
- Risk Assessment: Organizations must conduct a comprehensive risk assessment to identify potential risks and vulnerabilities to their systems and data. Risk assessment helps in determining the appropriate control measures and mitigation strategies to address the identified risks.
- Control Activities: Organizations must implement control activities to mitigate risks and ensure the effectiveness of their control environment. These activities include logical and physical access controls, change management procedures, data encryption, incident response protocols, and ongoing monitoring.
- Monitoring Services: Continuous monitoring of the control environment is crucial to detecting anomalies or potential security breaches. Organizations should establish monitoring services to track and review system logs, security events, and access logs to ensure the ongoing effectiveness of controls.
- Testing: Regular testing of controls is essential to validate their design and operating effectiveness. It includes performing internal testing, independent audits, and assessments to verify that controls are implemented as intended and are functioning properly.
- Third-Party Service Providers: Organizations must assess and manage the risks associated with third-party service providers. This involves conducting due diligence on the security practices and control environments of vendors and ensuring that appropriate agreements and controls are in place to protect customer data.
- Reporting: Organizations are required to produce a SOC 2 report that documents the results of their assessment. The report provides an overview of the control environment, control objectives, control activities, and the auditor’s opinion on the effectiveness of controls.
By meeting these SOC 2 requirements, organizations can demonstrate their commitment to data security and privacy, ensuring that the controls effectively protect customer data and align with industry standards and best practices.

THE BENEFITS OF AN SOC 2 AUDIT
A SOC 2 audit offers numerous advantages, including demonstrating regulatory compliance, building trust, gaining a competitive edge, managing risks, improving internal controls, and meeting customer expectations for data protection and privacy. A SOC 2 audit offers several key benefits:
- Demonstrating Compliance: SOC 2 audits validate an organization’s compliance with industry-specific data protection regulations and standards, ensuring adherence to legal requirements.
- Building Trust: The SOC 2 certification demonstrates a commitment to data security and privacy, enhancing trust and confidence among customers, partners, and stakeholders.
- Competitive Advantage: Being SOC 2 compliant sets organizations, showcasing their strong data protection practices and attracting customers who prioritize secure service providers to the competitors.
- Risk Management: SOC 2 audits help identify and mitigate risks associated with data breaches and privacy incidents, reducing the likelihood and impact of security breaches.
- Improved Internal Controls: Through SOC 2 audits, organizations can enhance their internal controls, policies, and procedures related to data protection, strengthening overall security posture.
- Assisting Organizations: SOC 2 audits support organizations in meeting customer requirements, expanding their customer base, and ensuring they have robust incident response plans in place.
WHAT IS THE SOC 2 COMPLIANCE CHECKLIST?
The SOC 2 compliance checklist provides thorough guidance for obtaining and maintaining SOC 2 compliance. While some stages are the same for all firms pursuing SOC 2 certification, precise tasks may differ depending on the scope of the report, the required report type, and the nature of the products and services provided. Typical universal stages include developing security policies, putting controls in place, conducting risk assessments, and undergoing audits. To ensure full compliance, the checklist should be adjusted to each organization’s specific circumstances. Organizations can successfully navigate the SOC 2 compliance process and avoid potential risks by carefully examining these aspects and tailoring the checklist accordingly.
1. SOC 2 planning and preparation: A customized checklist that will position you for success will help you get ready for your SOC 2 compliance journey. Establish specific goals that are based on the particular requirements of your company and learn about the Trust Services Criteria (Privacy, Confidentiality, Processing Integrity, Security, and Availability). Whether you need a snapshot assessment (SOC 2 Type 1) or a more in-depth analysis of ongoing controls (SOC 2 Type 2), choose the audit approach that best meets your needs.
The next step is to precisely identify the parameters that apply to your operations and specify the extent of your compliance activities. Create a strong communication network between important departments, such as HR, administration, and other crucial divisions, to promote internal synergy. By doing this, it is made sure that everyone is participating actively in the compliance process and staying on the same page.
To determine opportunities for improvement and to determine your organization’s current standing, conduct a complete readiness assessment. By adhering to this customized checklist, you’ll clear the route for a smooth and effective SOC 2 compliance, demonstrating to your stakeholders your organization’s dedication to data security and reliability.
2. Implementation of SOC 2 controls: Using a customized checklist that positions you for success, get ready for the path towards SOC 2 compliance. Create well-defined goals based on the particular needs of your business and educate yourself on the Trust Services Criteria, which include processing integrity, privacy, availability, security, and processing integrity. Decide which audit method best suits your needs, whether it’s a snapshot evaluation (SOC 2 Type 1) or a more in-depth examination of continuing controls (SOC 2 Type 2).
The next vital stage is to properly define the parameters that apply to your business and define the parameters that define the extent of your compliance efforts. To create internal synergy and guarantee active participation throughout the compliance process, foster effective communication networks between essential departments, such as HR, administration, and other crucial divisions.
Evaluate your organization’s present state and find areas for development by conducting a comprehensive readiness assessment. Following this personalized checklist will help you demonstrate to stakeholders your organization’s commitment to data security and dependability while paving the way for a simple and efficient path towards SOC 2 compliance.
3. SOC 2 audit: Once all the necessary controls have been put in place, it’s time to be ready for your SOC 2 audit.
- Collect Evidence: In order for your auditor to perform a comprehensive audit, gather all relevant paperwork and proof.
- Hire a SOC 2 auditor with the following qualifications: Choose an auditor from a respectable AICPA-accredited company to guarantee the legitimacy and experience required for your SOC 2 audit.
- Work together with the auditor: Keep lines of communication open with the auditor you have selected, and send them any additional files or information they need to complete the audit.
It is to be expected that a SOC 2 Type 2 audit will take longer than a SOC 2 Type 1 audit. Furthermore, ensure you have all the necessary paperwork ready, including a detailed statement detailing any changes you made to the system while it was under audit.
4. SOC 2 maintenance: Once SOC 2 compliance is attained, it must be sustained over time. This checklist aids in establishing a sustainable maintenance strategy. Use a trust management platform to enable continuous monitoring so that you can regularly assess your system for changes and compliance gaps. Make sure the monitoring solution you select is scalable, can compile documents, integrates with current workflows, sends out control discrepancy notifications, and offers full visibility into your security infrastructure. This proactive strategy promotes continuous adherence to SOC 2 standards by enabling the prompt discovery and correction of compliance concerns. You can effectively maintain compliance by incorporating these procedures into your operational framework, thereby protecting the integrity and reputation of your firm over time.
THE IMPORTANCE OF SOC 2 COMPLIANCE FOR DATA PRIVACY AND PROTECTION
SOC 2 compliance plays a crucial role in ensuring data privacy and protection for organizations. The key reasons why SOC 2 compliance is important for data privacy and protection are:
- Trust and Confidence: SOC 2 compliance demonstrates an organization’s commitment to safeguarding sensitive data. It assures customers, partners, and stakeholders that the organization has implemented robust controls to protect their information.
- Industry Recognition: SOC 2 compliance is increasingly becoming a requirement in various industries, especially for service providers that handle customer data. Achieving SOC 2 compliance helps organizations meet regulatory and contractual obligations, enhancing their reputation and competitiveness in the market.
- Comprehensive Evaluation: SOC 2 compliance involves a rigorous assessment of an organization’s internal controls and processes related to data protection. This evaluation goes beyond basic security measures, focusing on privacy, availability, and processing integrity. It ensures a holistic approach to data privacy and protection.
- Risk Mitigation: SOC 2 compliance assists organizations in identifying and mitigating risks associated with data privacy. Through regular audits and assessments, organizations can proactively identify vulnerabilities, implement necessary controls, and address potential threats to data privacy, reducing the risk of data breaches and unauthorized access.
- Customer Expectations: In today’s data-driven world, customers are increasingly concerned about the security and privacy of personal information. SOC 2 compliance serves as a clear signal to customers that data is handled with care, meeting their expectations for data privacy and protection.
- Internal Process Improvement: The process of achieving SOC 2 compliance requires organizations to evaluate and enhance their internal processes, policies, and procedures related to data privacy and protection. This exercise promotes a culture of security and privacy awareness within the organization, leading to better data-handling practices.
- Incident Response Readiness: SOC 2 compliance necessitates the establishment of incident response plans and procedures. By being prepared, organizations can swiftly and efficiently respond to data breaches or privacy incidents and minimize the potential impact on individuals’ privacy rights.
SOC 2 compliance is essential for organizations to demonstrate their commitment to data privacy and protection. It helps build trust with customers, ensures regulatory compliance, mitigates risks, and drives continuous improvement in data handling practices. By adhering to SOC 2 standards, organizations can enhance their data privacy posture and protect sensitive information from unauthorized access or disclosure.
ELIGIBILITY FOR SOC 2 CERTIFICATION
Organizations can demonstrate their commitment to upholding strong information security and protecting data privacy by obtaining SOC 2 accreditation. Service providers that serve other businesses, such as SaaS providers, cloud hosting companies, and data centers, are especially interested in it. In order to give their clients peace of mind about the security, availability, processing integrity, confidentiality, and privacy of their systems and data, these organizations work for SOC 2 certification.
Any firm handling sensitive data can benefit from SOC 2 accreditation; it’s not just for service providers. SOC 2 accreditation demonstrates an organization’s dedication to upholding strict data protection and security standards. Organizations can obtain it voluntarily to increase confidence or as a result of contractual requirements. In today’s networked digital environment, SOC 2 accreditation is essential for improving trust, credibility, and dependability.
HOW MUCH DOES SOC 2 CERTIFICATION COST?
The cost of SOC 2 certification depends on a number of factors, such as the organization’s size and complexity and the auditing firm selected. Typically, the cost ranges from a few thousand to tens of thousands of dollars. Larger firms with more complex systems typically incur higher costs. Aside from the fees paid to the auditing firm, there may be additional costs associated with correcting discovered flaws or defects during certification. Regardless of the expenses, gaining SOC 2 certification can provide considerable benefits by demonstrating a commitment to security and compliance for both consumers and stakeholders.
SOC 2 certification specifically costs $4,750 USD for organizations with one to twenty-five employees. This costs an additional 6750 USD for companies with 25–100 employees. And last, the price increases to 9750 USD for companies with 100–250 employees.
CHALLENGES AND SOLUTIONS IN SOC 2 CERTIFICATION
Challenges in SOC 2 certification include:
- Scope Determination: Defining the appropriate scope of the assessment and identifying the relevant trust services categories (TSCs) can be challenging.
- Control Implementation: Implementing and documenting controls that meet the SOC 2 compliance requirements can be time-consuming and resource-intensive.
- Gap Remediation: Addressing gaps and weaknesses identified during the assessment requires careful planning and implementing the corrective measures.
Solutions to confound these challenges include:
- Expert Guidance: Engaging experienced professionals or consultants who specialize in SOC 2 certification can provide valuable guidance in scoping, control implementation, and gap remediation.
- Clear Documentation: Thoroughly documenting control processes, policies, and procedures ensures clarity and compliance with SOC 2 requirements.
- Ongoing Monitoring: Establishing regular monitoring and internal audits helps ensure continuous compliance and identification of potential issues for prompt resolution.
HOW LONG DOES SOC 2 CERTIFICATION LAST?
Once an organization obtains SOC 2 certification, its validity extends for a specific period, typically one year. After this period, the organization needs to undergo a recertification process to maintain the validity of the certification. Recertification involves conducting an audit to ensure continued compliance with the SOC 2 criteria and requirements. Undergoing regular recertification allows organizations to showcase their ongoing dedication to upholding the essential controls and security practices specified in the SOC 2 framework. This periodic evaluation ensures that the organization’s systems and processes remain within the evolving security landscape and industry standards.
CERTPRO: EMPOWERING YOUR BUSINESS TO ATTAIN SOC 2 COMPLIANCE EFFORTLESSLY
CertPro, a trusted consulting firm, can assist your business in achieving SOC 2 certification. With their expertise and experience, CertPro will guide you through the process of meeting the rigorous requirements of SOC 2. They will conduct an in-depth assessment of your organization’s controls, policies, and procedures related to security, availability, processing integrity, confidentiality, and privacy. CertPro will help you identify gaps, develop remediation plans, and implement necessary improvements to align with SOC 2 standards. Their comprehensive approach ensures that your business meets the necessary criteria for SOC 2 certification, giving you a competitive edge, increased customer trust, and an improved security posture.
FAQ’s
HOW LONG WILL IT TAKE TO ACHIEVE SOC 2 COMPLIANCE?
The timeframe to achieve SOC 2 compliance varies depending on the organization’s readiness and the complexity of its control environment. It can range from several months to a year or more, considering the time required for gap analysis, control implementation, testing, and audit preparation.
WHICH IS BETTER SOC 1 OR SOC 2?
SOC 1 and SOC 2 primarily distinguish themselves by their focal points. While SOC 1 reports primarily manage financial data, SOC 2 reports encompass a broader array of topics, including availability, security, processing integrity, confidentiality, and privacy.
WHAT ARE THE SOC 2 CONTROLS?
SOC 2 controls are the procedures, policies, and technology measures put in place to prevent and detect security breaches, thereby strengthening your information security standards. They help to anticipate and detect potential security flaws.
WHAT IS THE CONSEQUENCE OF SOC 2 NON-COMPLIANCE?
Consequences of SOC 2 non-compliance include loss of customer trust, reputational damage, potential legal and regulatory penalties, increased security risks, an inability to attract new customers, and limited business opportunities due to non-compliance with industry standards and customer requirements.
IS SOC 2 CERTIFICATION MANDATORY?
Although SOC 2 certification is not necessary, customers, business partners, or regulatory bodies frequently request it in order to evaluate an organization’s control environment. Obtaining SOC 2 certification can enhance an organization’s credibility, trustworthiness, and competitiveness.
HOW CAN STARTUPS ATTAIN SOC 2 COMPLIANCE IN 2024?
Trust is crucial for startups to do well in today's digital world. It's vital for establishing credibility with clients, especially in a data-driven environment where privacy is the main component. Therefore, getting a SOC 2 compliance report is crucial to building...
SOC TOOLS: How They Impact On Security Aspect Of The Organization
The changing cybersecurity landscape increases the importance of Security Operations Center (SOC) tools. Hence, it is essential for strengthening digital defenses and protecting against cyberattacks. SOC tools help security teams detect, monitor, and prevent security...
WHAT IS SOC FOR CYBERSECURITY?
In today's fast-paced digital landscape, ensuring robust cybersecurity measures is imperative for organizations aiming to protect sensitive data and maintain stakeholder trust. The American Institute of CPAs (AICPA) crafted the SOC for cybersecurity reporting...



