Cybersecurity is now an essential criterion of existence for businesses. When we discuss cybersecurity assessments, SOC 2 compliance comes to mind. It is an information security framework that helps with data security. Therefore, organizations must secure their private data from cyberattacks or misuse. The SOC 2 compliance process requires a risk assessment program. Consequently, SOC 2 risk assessment helps recognize an organization’s potential vulnerabilities. In addition, based on the findings, you can take proactive measures to mitigate the risk and continue the operational process. Thus, risk assessment helps the organization comply with industry-related rules and regulations.
This article will discuss risk assessment in detail. How it is working and why it is crucial for your business. At the end of the article, we will discuss the implementation process of risk assessment that will surely help your business.
What is SOC 2 risk assessment?
SOC 2 risk assessment recognizes the risks of information security systems and assesses their impact. Furthermore, risk assessment helps implement security postures to mitigate risks. The evaluation requires the auditor’s supervision and guidance. The auditor evaluates the organization’s control regarding the selected trust service criteria. The process is quite complicated and time-consuming. Therefore, an internal audit is required before the external or final auditing process. During the external audit process, the auditor reviews the policies and procedures of the organizations. In addition, the compliance report also includes interviewing the employees and identifying the controls’ effectiveness.
The main aim of the risk assessment is to prevent non-compliance and improve the organization’s reputation. Adherence to compliance suggests that the organization prioritizes data security. Thus, it helps maintain trust and dependency among stakeholders and clients.
IMPORTANTANCE OF SOC 2 RISK ASSESSMENT?
SOC 2 risk assessment helps in mitigating emerging risks and preventing reputational damage. The other significances are discussed below:
- Information security framework: If your organization handles and manages sensitive customer data, SOC 2 compliance is important. Therefore, the compliance process helps to recognize your organization’s vulnerability regarding data security, availability, and integrity. Thus, a SOC 2 compliance report suggested that the organization effectively follows the industry-related security posture.
- Risk Management: The risk assessment process helps yoo identify risks that threaten the operation and reputation of your organization. The process can help your organization reduce security breaches and data loss incidents. Moreover, the process ensures that data availability decreases downtime and that policies and procedures are reliable.
- Competitive Advantage: The SOC 2 compliance report signifies that the organization prioritizes data security and privacy. Thus, it helps create trust and dependency among the customers and stakeholders. On the other hand, an organization can showcase its efforts in data security to develop new business connections. Moreover, SOC 2 compliance improves business and growth.
- Customer Trust: Trust is essential for the sustainability of businesses. Therefore, consecutive cyberattacks and data breaches are increasing customer’s concerns regarding data security and privacy. Thus, the SOC 2 compliance report helps organizations build trust with their customers and assure them of their data security and privacy.
In brief, SOC 2 risk management helps organizations manage their data processing and handling risks. It prevents data breaches and non-compliance with regulations and creates trust among customers and stakeholders.
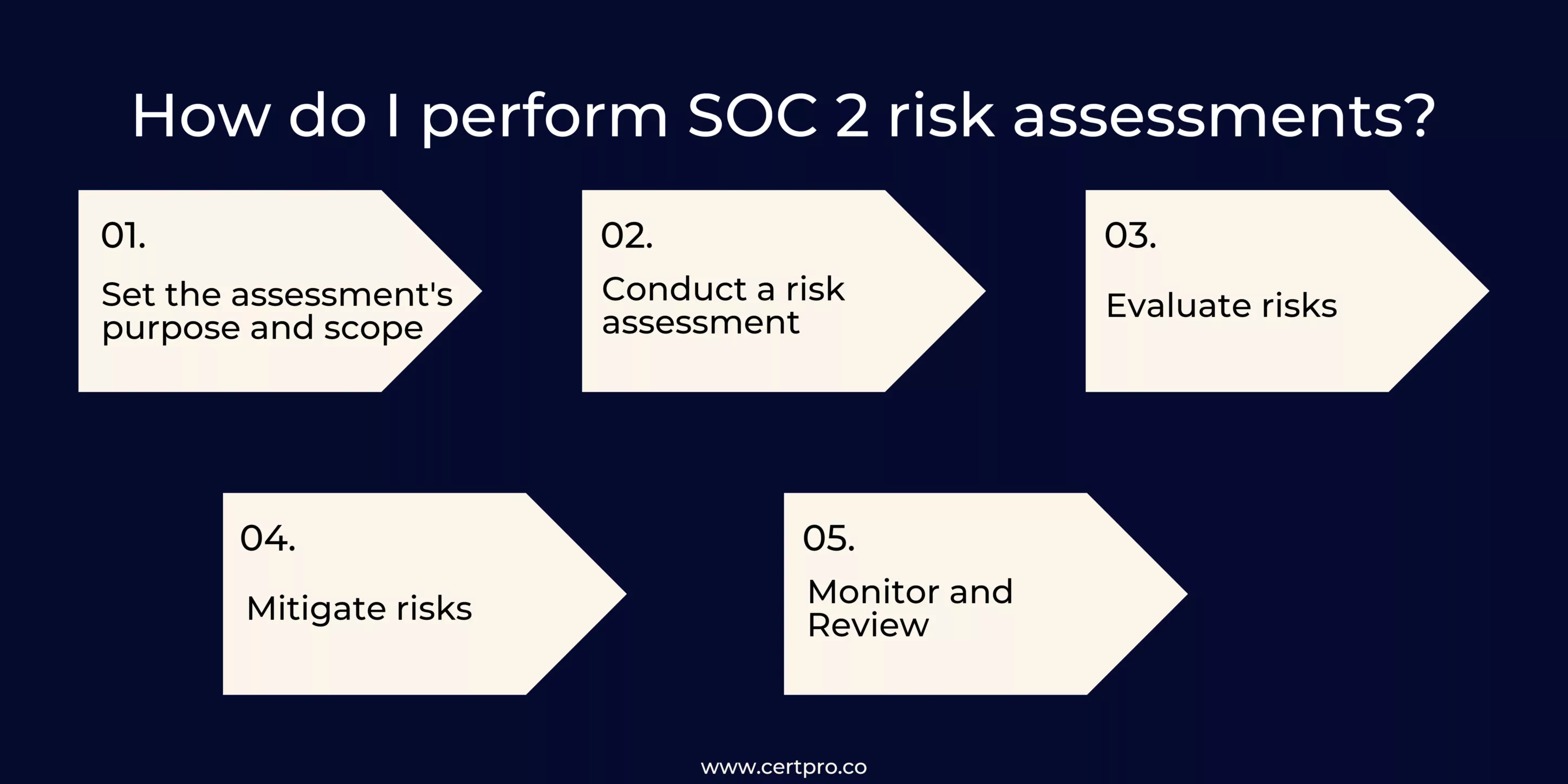
How do I perform SOC 2 risk assessments?
SOC 2 risk assessment is a complex SOC 2 compliance process step. Generally, it requires identifying your business’s risks and vulnerabilities. In addition, the process presumes the risks’ impact and deploys a mitigation process to manage them. Every organization must undergo a risk assessment, as identical risks are uncommon in the same industry. Now, we will discuss how to perform a SOC 2 risk assessment using the SOC 2 risk assessment template:
- Set the assessment’s purpose and scope: At the initial assessment stage, you must identify the business goal and objectives. The objective signifies your commitment to your customers and prospects. Therefore, you should select trust service criteria that mainly focus on the organization’s commitment. Suppose your organization handles customers’ sensitive data and is committed to the non-disclosure agreement. Thus, the trust service criteria should select the confidentiality and security for SOC 2 risk assessment. However, in SOC 2, common security is the standard and mandatory criteria, and you need to select more for better compliance. On the other hand, if your organization is managing online data resources, data integrity is a significant commitment to avoid downtime. Hence, the scope and purpose of risk assessment should align with the organization’s commitment to its clients and stakeholders.
- Conduct a risk assessment: The risk assessment process recognizes the risk associated with your organization’s controls and procedures, while the reviewing process recognizes gaps or vulnerabilities within the controls. In this step, you will determine your business’s risk related to vendor management and partners. It includes employee misuse of data, managerial changes, or technological changes. In addition, you can recognize the risks related to production infrastructure, endpoint risks, and data access-related risks.
- Evaluate risks: In the next step, categorize the risks based on their impact. The SOC 2 risk assessment template can help you evaluate each risk. The template includes a scoring system that you can use to assess the likelihood and potential impact of each risk. The effect could be legal, financial, regulatory, or reputational. You can assign a score to each risk based on its likelihood and potential impact and then prioritize the risks based on their scores.
- Mitigate risks: Once you have evaluated them, the next step is mitigating them. This involves implementing controls to reduce each risk’s likelihood and potential impact. You can use the SOC 2 vendor risk assessment template to help you evaluate the controls that your vendors have in place. The SOC 2 risk assessment template is a comprehensive tool that enables you to assess your vendors’ controls to mitigate security, availability, processing integrity, confidentiality, and privacy risks. The template includes a list of potential controls and a description of each control and its effectiveness.
- Monitor and Review: Finally, monitoring and reviewing the effectiveness of your implemented controls is essential. This involves regularly reviewing the controls to ensure that they are still effective and identifying any new risks that may have emerged. You can use the risk assessment template to help you monitor and review your controls.
It can be concluded that performing the SOC 2 assessment is crucial for compliance. Therefore, an effective risk assessment template helps streamline the assessment process. In addition, regular monitoring of the controls ensures that the organization adheres to compliance.
THE DIFFERENCE BETWEEN SOC 2 RISK ASSESSMENT AND RISK MANAGEMENT
Risk management helps address and monitor your organization’s risk controls. It enables you to identify, evaluate, and report risk-related concerns. Consequently, it is a continuous process of tracking risk from multiple risk sources. It includes risk assessments, addressing the gaps between the existing controls, and complying with them. In general, risk assessment is a one-time exercise. However, it is a standalone exercise that provides an idea of the risks. Risk assessment also helps recognize compliance standards. In addition, a questionnaire can be prepared for risk assessment to identify security controls.
Expert Guidance for SOC 2 Risk Assessment
SOC 2 compliance is a security framework for your organization. Therefore, SOC 2 risk management helps recognize the efficacy of implemented controls. The process also identifies vulnerabilities and gaps in the policies and procedures. Thus, your organization may need help conducting the assessment. In this condition, you might seek assistance from experts. CertPro is a reputed auditing and consulting firm that implements safety and regulatory compliance. We can help you in your SOC 2 journey with our knowledge and guidance. Furthermore, CertPro assists your organization in identifying and mitigating risks to meet industry standards. Overall, CertPro can play a vital role in helping organizations conduct SOC 2 risk assessments and improve their security posture, which is essential in today’s digital landscape.
FAQ
What are the requirements for the SOC 2 risk assessment?
SOC 2 assessment has several requirements that organizations must meet to ensure its effectiveness. Firstly, the organization must define the scope of the assessment, including identifying the systems, processes, and data that are in scope for the assessment. Secondly, the organization must select the appropriate Trust Services Criteria (TSC) that align with their business objectives and assess the effectiveness of controls against those criteria. Other requirements include identifying and documenting controls, testing the effectiveness of controls, preparing a report summarizing the results of the assessment, and establishing a process for continuous monitoring of the effectiveness of controls.
What is the purpose of SOC 2 risk assessment?
Who can perform SOC 2 risk assessment?
What are the benefits of SOC 2 risk assessment?
How much does a SOC 2 report cost?

About the Author
SUBBAIAH KU
Subbaiah Ku is the Regional Director for CertPro in Oman, bringing a wealth of expertise in process and system auditing. As a seasoned lead assessor, Subbaiah is dedicated to ensuring the highest standards in compliance and security. His unique blend of technical acumen, rooted in Mechanical Engineering, is complemented by a diverse range of certifications and extensive training.
HOW CAN STARTUPS ATTAIN SOC 2 COMPLIANCE IN 2024?
Trust is crucial for startups to do well in today's digital world. It's vital for establishing credibility with clients, especially in a data-driven environment where privacy is the main component. Therefore, getting a SOC 2 compliance report is crucial to building...
SOC TOOLS: How They Impact On Security Aspect Of The Organization
The changing cybersecurity landscape increases the importance of Security Operations Center (SOC) tools. Hence, it is essential for strengthening digital defenses and protecting against cyberattacks. SOC tools help security teams detect, monitor, and prevent security...
WHAT IS SOC FOR CYBERSECURITY?
In today's fast-paced digital landscape, ensuring robust cybersecurity measures is imperative for organizations aiming to protect sensitive data and maintain stakeholder trust. The American Institute of CPAs (AICPA) crafted the SOC for cybersecurity reporting...




