The healthcare industry has experienced tremendous change in the current era of digital connectivity. Cyberthreats increasingly target the healthcare sector due to the wide range of sensitive data that is maintained online, including insurance details and medical histories. Understanding the nuances of healthcare data breaches is crucial in this regard for patients and healthcare professionals alike.
One of the biggest problems facing the modern healthcare system is healthcare data breaches. Unauthorized access, theft, or disclosure of private patient data kept in billing records, electronic health records, and other digital platforms are all included in these breaches. Because of this, they seriously jeopardize patient privacy and the integrity of medical procedures. With multiple occurrences reported each year, the prevalence of medical data breaches is startling. Over 500 of these hacks were reported in 2023 alone, affecting millions of patient records from numerous healthcare institutions and organizations. Numerous methods, such as complex cyberattacks, insider threats, and the actual theft of equipment holding private information, can lead to these breaches.
Beyond the information that was stolen, healthcare data breaches have far-reaching effects. The financial fallout is substantial, with breach-related expenses surpassing $9 million on average for each event. These costs include the cost of the inquiry, the corrective action, the legal fees, and the possible fines for breaking regulations. Additionally, violations weaken patient confidence in medical professionals, impeding candid dialogue and jeopardizing the standard of care. Proactive steps are necessary to address the threat of data breaches in healthcare. Prioritizing cybersecurity requires healthcare firms to put in place strong procedures, carry out frequent risk assessments, and encourage a culture of data security awareness among their employees. The three most important defenses against illegal access and data compromise are encryption, multi-factor authentication, and secure data storage.
In today’s digital healthcare environment, medical data breaches essentially pose a serious concern. Stakeholders can strengthen patient data security and integrity and protect confidentiality and public trust in healthcare services by identifying the extent of the issue, acknowledging its effects, and putting effective preventive measures in place.
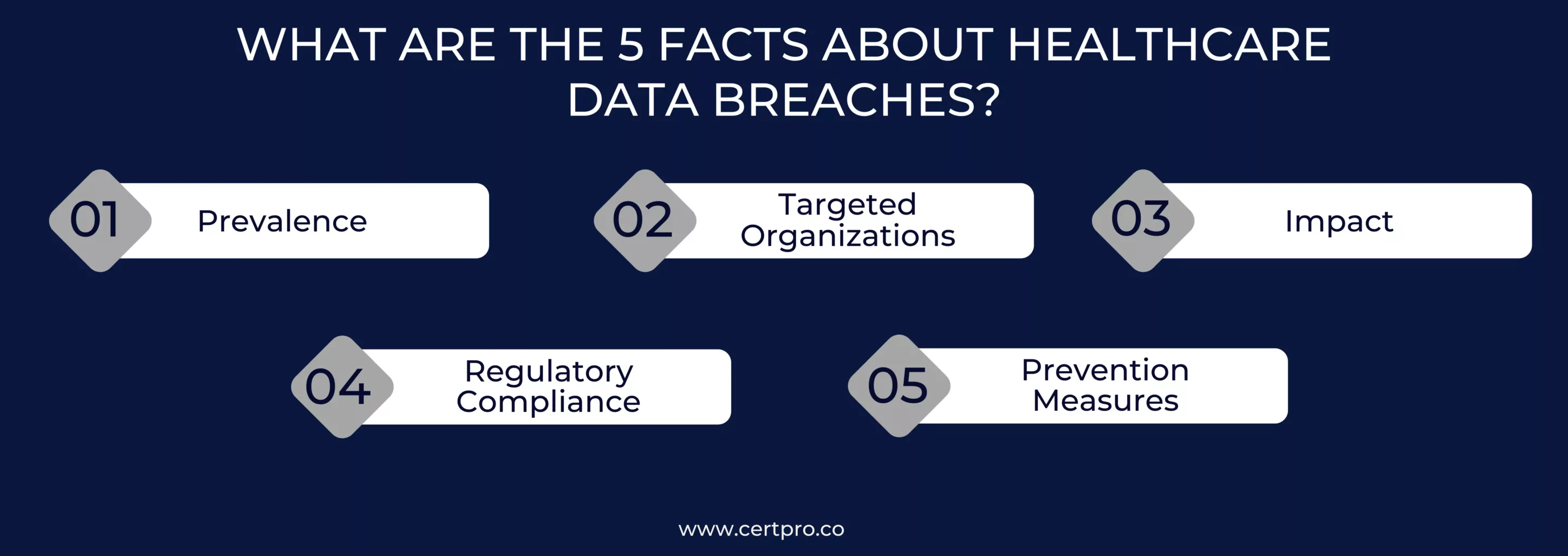
WHAT ARE THE 5 FACTS ABOUT HEALTHCARE DATA BREACHES?
Data breaches in the healthcare sector are a significant challenge to the industry, as they have become more common in recent years. This trend highlights the importance of comprehending several aspects of these breaches, including their frequency, effects, and preventative actions. Healthcare businesses can strengthen their ability to protect patient data and uphold confidence in their services by exploring these facts.
1. Prevalence: Reports of healthcare data breaches have been frighteningly frequent, with a notable increase in events in recent years, according to studies. These breaches impact millions of patient records every year, underscoring the pervasive vulnerability of healthcare data systems. This prevalence emphasizes how urgently strong security measures are needed to reduce the possibility of unauthorized access and shield private patient data from misuse.
2. Targeted Organizations: The primary targets of medical data breaches are healthcare clearinghouses, business associates, health plans, and healthcare providers. Healthcare providers are among these institutions that experience a disproportionately high number of incidents and are constantly the target of breaches. This pattern emphasizes how critical it is to strengthen security measures throughout the healthcare ecosystem in order to effectively reduce risks and preserve patient data.
3. Impact: Financial losses, legal ramifications, and a decline in public confidence in impacted businesses are just a few of the consequences of medical data breaches, which go far beyond stolen data. Furthermore, breaches could put patients at risk for fraud or identity theft, which would worsen the effects on them. As such, the fallout from breaches emphasizes how important it is to have strict security processes and quick reaction times in order to reduce damage and rebuild trust in healthcare services.
4. Regulatory Compliance: The Health Insurance Portability and Accountability Act (HIPAA) is one of the main regulatory frameworks that healthcare firms must operate under. Adherence to data protection legislation is crucial, as noncompliance can lead to serious sanctions and harm to one’s reputation. Thus, upholding regulatory compliance is essential to retaining patient trust and guaranteeing the integrity of healthcare systems, in addition to being required by law.
5. Prevention Measures: Reducing the likelihood of data breaches in healthcare requires taking proactive steps. Fortifying defenses against potential threats requires putting in place strong cybersecurity policies, regularly conducting risk assessments, and offering extensive staff training on data security best practices. Furthermore, by preventing unwanted access and protecting patient confidentiality, healthcare infrastructures can be made more resilient by utilizing encryption, multi-factor authentication, and secure data storage technologies.
TYPES OF DATA BREACHES IN HEALTHCARE
Data breaches in the healthcare industry seriously threaten patient privacy and the reliability of medical systems. These breaches come in a variety of forms, each with its own special traits and ramifications. Healthcare companies must comprehend many types of data breaches in healthcare to put in place strong security measures and safeguard private patient data. Every kind of breach, from physical theft to illegal access, has unique difficulties that call for preventative measures. Stakeholders can gain a better understanding of the challenges involved in protecting patient data and work toward improving the security posture of the healthcare sector by looking at the different types of data breaches in healthcare that occur frequently in the sector.
1. Cyberattack/IT incident: Cyberattacks and IT incidents refer to the unlawful use of malicious software, such as malware, phishing, or SQL injection, to gain access to networks or healthcare systems. These breaches pose significant threats to privacy and trust, affecting patient data contained in electronic health records (EHRs) and other systems. Attackers typically target unpatched systems or weak passwords by taking advantage of flaws in software or hardware. To identify and stop these kinds of problems, healthcare institutions need to put strong cybersecurity safeguards in place. These measures include firewalls, encryption, and staff training. To minimize risks and protect patient data and confidence, regular security evaluations and incident response procedures are essential.
2. Unauthorized access/disclosure: Unauthorized access or disclosure happens when people or organizations obtain sensitive patient data improperly and without the required authorization. Numerous things, including shoddy security protocols, insider threats, and unintentional exposures, could lead to this breach. It jeopardizes the privacy of patient data kept in databases, electronic health records (EHRs), or other medical systems, which may result in financial fraud, identity theft, or harm to one’s reputation. Physical breaches, social engineering, and hacking are some ways that unauthorized entry might happen. To avoid unauthorized access and disclosure, healthcare organizations need to implement stringent access controls, encryption, and employee training. Respecting laws such as HIPAA is necessary to reduce hazards and safeguard patient confidentiality and confidence.
3. Theft: Theft in healthcare is defined as the unlawful taking or removal of physical devices or papers that hold sensitive patient information. This breach compromises the confidentiality and security of patient data and can occur as a result of the theft of laptops, smartphones, or paper records from healthcare facilities, vehicles, or employees’ residences. Stolen devices or documents may contain electronic health records (EHRs), billing information, or other sensitive data, putting patients at risk of identity theft or fraud. To avoid theft and secure patient information, healthcare organizations must put in place measures such as encryption, physical security controls, and inventory tracking. Prompt reporting and cooperation with law enforcement are critical in reducing the impact of theft occurrences on patient privacy and trust.
4. Loss: In the healthcare industry, “loss” refers to the unintended misplacing or disappearance of tangible objects or papers that hold private patient data. This breach endangers patient data security and confidentiality, which can result from various factors such as carelessness, human error, or inadequate security measures. Electronic devices that could be misplaced include computers, smartphones, USB drives, and paper records that hold personal information such as billing information or electronic health records (EHRs). Patients run the danger of identity theft, fraud, and illegal access if such goods are lost. To minimize loss and preserve patient information, healthcare institutions need to have policies in place, including inventory tracking, encryption, and employee training. Minimizing the impact on patient privacy and confidence requires prompt reporting of loss instances and careful investigation.
5. Improper disposal: Careless treatment of physical or electronic materials containing patient information during disposal, which could result in illegal access or disclosure, is referred to as improper disposal in the healthcare industry. An incorrect way to dispose of medical equipment, not deleting data from outdated devices, or discarding documents without shredding are a few healthcare data breach examples. Organizations need to implement safe disposal practices, like shredding papers, cleaning electronics, and properly discarding medical equipment, in order to reduce dangers. For the purpose of guaranteeing compliance and protecting patient privacy, staff supervision and training are critical.
WHAT TYPES OF ORGANIZATIONS ARE IN DANGER OF HEALTHCARE DATA BREACHES?
The Department of Health and Human Services (HHS) tracks data breaches across four main types of organizations within the healthcare industry: healthcare providers, health plans, business associates, and healthcare clearinghouses.
1. Healthcare Providers: Organizations that provide medical care to people include clinics, hospitals, doctor offices, assisted living facilities, and other establishments. Healthcare professionals handle sensitive patient data, including personal identifiers, medical records, and treatment histories. In order to preserve patient privacy and adhere to legal obligations such as the Health Insurance Portability and Accountability Act (HIPAA), they are in charge of guaranteeing the security and confidentiality of this data.
2. Health plans: Health plans, sometimes referred to as insurance carriers or payers, are organizations that cover medical costs. Examples of these include managed care organizations, government-sponsored health programs like Medicare and Medicaid, and health insurance firms. Health plans gather and save a lot of data about their policyholders, such as coverage specifics, claim history, and demographic data. To stop fraud, identity theft, and unauthorized access, sensitive data must be protected.
3. Business Associates: Companies that provide services or execute specific tasks involving access to protected health information (PHI) on behalf of healthcare providers or health plans are known as business associates. These could be independent contractors, consultants, billing firms, and IT support providers. Business associates must abide by HIPAA rules and execute contracts specifying their obligations to protect PHI. Both the business partner and the covered entity may face severe penalties for failing to protect PHI.
4. Healthcare clearinghouses: These organizations handle and enable the electronic interchange of medical data between various organizations, including government agencies, health insurance, and physicians. Clearinghouses frequently carry out tasks including electronic transaction routing, claim information verification, and data format translation. Clearinghouses are essential to maintaining the safe and effective flow of healthcare data, even though they often do not generate or keep PHI. Clearinghouses are subject to HIPAA laws, much like other entities in the healthcare ecosystem, in order to safeguard the integrity and confidentiality of patient data.
HOW DO HEALTHCARE FIRMS PREVENT DATA BREACHES?
1. Examine current security risks: Providers must conduct an annual security risk assessment in compliance with HIPAA standards in order to find vulnerabilities and revise policy. Make sure that frequent security audits are a top priority, and resist the urge to expedite or skip them.
2. Maintain an incident response plan: Creating and implementing a response plan can prevent escalations in the event of an incident or breach. This strategy offers precise instructions for making important choices and carrying out required follow-up tasks.
3. Provide continuing education: Employees should be regularly trained on the most recent HIPAA rules and regulations to make sure they understand the seriousness of data breaches and the consequences of non-compliance.
4. Limit access to medical records: It’s critical to recognize users, keep an eye on their activities, and enforce appropriate login protocols in a healthcare business with a large number of people and devices. Make sure that user role-based access permissions are applied effectively to limit access to medical records to authorized healthcare professionals exclusively.
5. Avoid using outdated IT infrastructure: Older devices are more vulnerable to hacking; therefore, upgrading outdated equipment on a regular basis decreases the chance of medical data breaches.
6. Update your software regularly: Hackers are constantly looking for new ways to access data. Regular software upgrades fix system weaknesses, lowering the danger of cyberattacks. With considerable experience in healthcare software development, the Demigod team can help you upgrade your medical solutions to meet current cybersecurity concerns.
7. Restrict use of personal devices: Healthcare staff typically use personal devices for remote access, which introduces extra concerns such as malware penetration and exposure to attacks. If you allow personal device use for work, create a strict policy outlining allowed devices, network connections, and usage protocols.
8. Encrypt data: Encryption technologies help to mitigate the damage of cyberattacks. According to HIPAA’s Breach Notification Rule, encrypted data is not considered unsecured; hence, its loss does not constitute a breach. While issues still demand attention, encryption can help avoid potential penalties from federal agencies.
9. Create a wireless network for guests: Creating a subnetwork is the most secure way to give patients and visitors Wi-Fi access while preventing access to your whole network.
10. Invest more in your security: In addition to strong network security tools, budget for your IT and legal departments. Ensure that your IT staff focuses on both digitalization and security modeling without favoring one over the other. Consider taking a proactive approach to preparing for prospective attacks with the legal team.
FAQ
What are the most common causes of healthcare data breaches?
Common causes include employee errors, negligence, unauthorized access, and data theft by insiders. Enhanced training and technology for access monitoring help mitigate these breaches.
Which cyber-risk framework is specific to healthcare?
HIPAA, the Health Insurance Portability and Accountability Act, mandates cybersecurity measures for safeguarding electronic health information and ensuring its privacy within healthcare organizations.
Are there any recent advancements or innovations in cybersecurity that healthcare organizations should consider adopting to enhance their data protection measures?
Healthcare organizations should consider adopting advancements such as artificial intelligence for threat detection, blockchain technology for secure data exchange, and advanced endpoint security solutions to enhance data protection measures.
What are some emerging trends in healthcare data breaches that organizations need to be aware of?
Emerging trends in medical data breaches include increased targeting of smaller healthcare providers, ransomware attacks, and sophisticated social engineering tactics.
How can healthcare providers effectively balance digitization efforts with maintaining robust security measures?
Healthcare providers can balance digitization efforts and security measures by implementing robust access controls, encryption technologies, and regular security assessments.

About the Author
ANUPAM SAHA
Anupam Saha, an accomplished Audit Team Leader, possesses expertise in implementing and managing standards across diverse domains. Serving as an ISO 27001 Lead Auditor, Anupam spearheads the establishment and optimization of robust information security frameworks.
HITECH ACT AND ITS IMPACT ON MODERN HEALTHCARE
In 2009, the Health Information Technology for Economic and Clinical Health or HITECH Act was signed to transform the American healthcare industry. The laws worked as a forward-thinking process of changing patient services. In this regard, the Patient Protection and...
BEST PRACTICES FOR DATA PROTECTION IN THE HEALTHCARE INDUSTRIES
In the healthcare sector, safeguarding sensitive information about patients is extremely important. Patient data includes personal details, medical histories, and treatment plans. Therefore, it must be protected and should be confidential. Thus, breaches not only...
HIPAA CONSULTANTS: WE KNOW HOW TO SECURE YOUR INFORMATION
Navigating HIPAA compliance can be complex; therefore, organizations seek advice from HIPAA consultants. These HIPAA experts have specific knowledge. They can help firms to understand the problematic standards of the Healthcare Privacy Act. In 1996, HIPAA was created....




