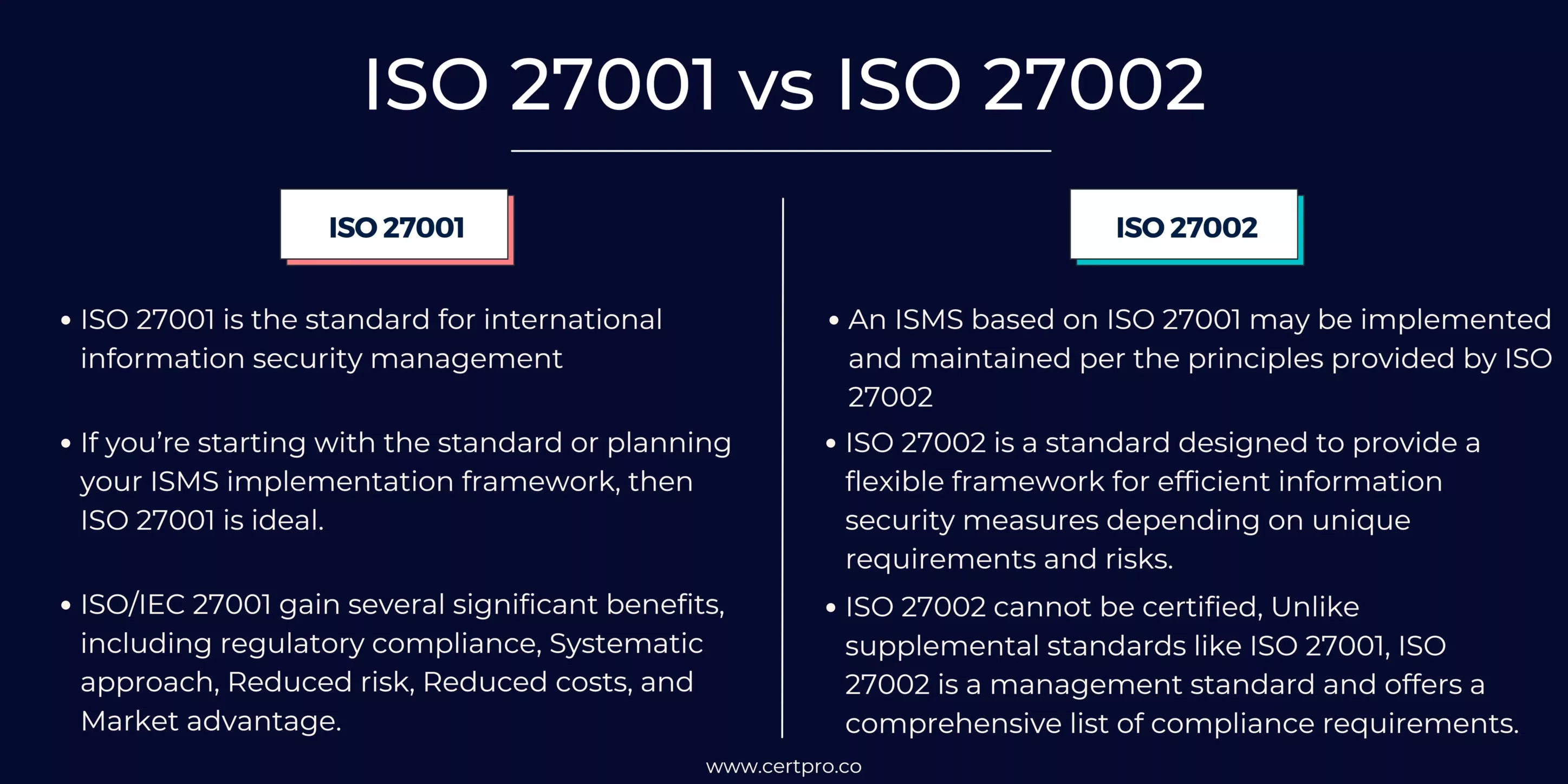
The International Organization for Standardization (ISO) has released two information security standards, ISO 27001 and ISO 27002. Despite their similarity, they have different functions.
ISO 27001 lays forth the requirements for an information security management system (ISMS) and offers a framework for handling sensitive data, safeguarding its integrity, and ensuring the accessibility of information assets. It provides a systematic approach for identifying, assessing, and managing information security risks.As a code of practice for information security management, ISO 27002 contrasts this. For starting, putting into practice, sustaining, and enhancing information security management in an organization, it offers guidance and general principles. An efficient information security management system can be established and maintained using the rules and best practices outlined in ISO 27002.
What is ISO 27001?
ISO 27001 is a widely accepted information security management standard that provides a framework for handling and safeguarding private and sensitive data within an organization. It outlines the processes for establishing, implementing, maintaining, and improving an ISMS. It is designed to assist businesses of all types and sizes in managing the security of their information assets, such as data, intellectual property, financial data, and customer information.
What is ISO 27002?
ISO 27002, previously known as ISO/IEC 17799 before its revision, is a standard that organizations can use to implement and maintain an ISMS based on ISO 27001. It breaks down the controls into 14 major groups, including information security policies, organization of information security, human resource security, asset management, access control, cryptography, physical and environmental security, operations security, communications security, system acquisition, development, and maintenance, supplier relationships, information security incident management, elements of business continuity management related to information security, and compliance. It provides a flexible framework for organizations to establish and maintain effective information security measures based on their unique requirements and risks.
Clauses 5–18 of ISO 27002 break down the controls into 14 major groups:
- A.5. Information security policies
- A.6. Organization of information security
- A.7. Human resource security
- A.8. Asset Management
- A.9. Access Control
- A.10. Cryptography
- A.11. Physical and environmental security
- A.12. Operations Security
- A.13. Communications Security
- A.14. System acquisition, development, and maintenance
- A.15. Supplier relationships
- A.16. Information security incident management
- A.17. Elements of business continuity management related to information security
- A.18. Compliance
According to their unique demands and risks, the standard is meant to give organizations a flexible framework to set up and maintain efficient information security measures.
Why are they important (ISO 27001, ISO 27002)?
ISO 27001 is important because it helps organizations safeguard the privacy, integrity, and data of their information assets. By conducting a risk assessment, organizations can identify potential hazards and implement risk mitigation or risk treatment measures. Risk management is the core principle of ISO 27001, which involves identifying risks and addressing them through security controls.
ISO 27002 is important as it provides a flexible framework for organizations to establish and maintain effective information security measures based on their unique requirements and risks. By implementing the ISO 27002 standard, organizations demonstrate their commitment to information security and ensure the confidentiality, integrity, and accessibility of their information assets.
What is ISMS?
ISMS stands for Information Security Management System, which is a framework of rules, practices, and guidelines designed to protect the accessibility, confidentiality, and integrity of sensitive data held by an organization.
Why do we need ISMS?
Implementing an ISMS can help organizations in several ways:
- Compliance with legal requirements: Numerous laws, rules, and contractual obligations govern information security. The good news is that by applying ISO 27001, the majority of issues can be fixed.
- Competitive advantage: If your business receives certification, you might stand out from the competition in the eyes of customers who care about the security of their personal data.
- Cost savings: The primary goal of ISO 27001 is to reduce security incidents. Money is spent on every incident, no matter how big or minor. Your business will save money if you can avoid them.
- Process improvement: Fast-growing businesses often lack the time to pause and clearly define their processes and procedures, which leaves staff members in the dark about who should do it, when, and how. By pushing businesses to document their primary operations, ISO 27001 implementation aids in the resolution of such issues.
How does ISMS work?
The ISMS is a methodical approach to handling sensitive company data safely. It includes people, procedures, and technology to offer a thorough method of protecting sensitive data within an organization. An ISMS’s main objectives are:
- Risk management
- guarantee the availability
- Confidentiality
- The integrity of the organization’s information assets
The policies and procedures that make up an ISMS are often created to handle the risks related to information security. Physical security measures (like access controls and security cameras), technical security measures (like firewalls and encryption), and administrative security measures (like rules and procedures) can all be included in these controls.
Industry standards and frameworks, such as ISO/IEC 27001, the NIST Cybersecurity Framework, or COBIT, are frequently used as a guide for implementing an ISMS. These frameworks offer recommendations and best practices for putting information security management systems into place.
ISO 27001 vs. ISO 27002: How do they differ from each other?
The ISO 27001 standard defines the standards for an information security management system (ISMS). An ISMS is a methodical strategy for handling sensitive data to guarantee its availability, confidentiality, and integrity. Using the ISO 27001 framework, organizations can create, implement, manage, and continuously improve an ISMS. It also contains a list of controls that businesses can use to reduce security risks.
However, ISO 27002 cannot be certified. This is so because, unlike supplemental standards like ISO 27001, ISO 27002 is a management standard and offers a comprehensive list of compliance requirements. ISO 27002 is a code of conduct for managing information security. For starting, putting into practice, sustaining, and enhancing information security management in an organization, it offers guidance and general principles. When adopting an ISMS, it’s important to keep in mind that not all information security measures will be applicable to your company.
That is abundantly clear from ISO 27001, which requires businesses to conduct a risk analysis to identify and rank information security threats. If you were to read ISO 27002 on its own, it would be nearly impossible to determine which controls you should implement because it makes no mention of this.
ISO 27002 offers instructions for managing information security, whereas ISO 27001 is a standard for creating an information security management system. Despite being related, they have diverse functions and work well together. Using ISO 27002 as a guide, the controls outlined in ISO 27001 can be implemented.
How and when to apply each standard?
The goals of ISO 27001 and ISO 27002 are distinct, and they can be useful in various situations.
ISO 27001 is the best option if you’re just getting started with the standard or developing your ISMS implementation framework. Once you’ve determined the controls you’ll be applying, you should consult ISO 27002 to understand more about how each one operates.To achieve these standards, CertPro can offer a range of services, including assessment, gap analysis, policy development, implementation guidance, and training.
CertPro’s assessment and gap analysis services can help your organization identify gaps in your current information security posture and determine what additional controls need to be implemented to meet the requirements of ISO 27001 and ISO 27002. CertPro can also help you develop policies and procedures to ensure that your organization meets the requirements of ISO 27001 and ISO 27002.
In addition to policy development, CertPro can provide implementation guidance to help your organization implement the necessary controls to meet the requirements of ISO 27001 and ISO 27002.
Finally, CertPro can provide training to your employees to ensure that they understand the importance of information security and the role they play in protecting your organization’s assets. This training can include general awareness training, role-based training, and technical training to ensure that your employees have the knowledge and skills necessary to protect your organization’s information assets.
FAQ
Are ISO 27001 and ISO 27002 related?
Yes, ISO 27001 and ISO 27002 are related to each other. ISO 27002 provides guidelines for implementing and maintaining an information security management system (ISMS), while ISO 27001 specifies the requirements for an ISMS. The intended use of ISO 27002 is to provide a reference for implementing the controls required by ISO 27001. The two standards are part of the ISO/IEC 27000 family of standards, which provides a framework for information security management.
How do ISO 27001 and ISO 27002 relate to other ISO standards?
ISO 27001 and ISO 27002 are part of the ISO/IEC 27000 family of standards, which includes a number of other standards related to information security management. Some examples include ISO 27003, which provides guidelines for the implementation of an ISMS; ISO 27004, which provides guidance on the measurement of information security; and ISO 27005, which provides a framework for information security risk management. Together, these standards provide a comprehensive approach to information security management.
Do companies need to implement both ISO 27001 and ISO 27002?
No, it is not necessary for companies to implement both ISO 27001 and ISO 27002. ISO 27001 is a certification standard that sets out the requirements for an information security management system (ISMS), while ISO 27002 provides guidelines for implementing and maintaining an ISMS. However, ISO 27002 can be used as a useful reference for implementing the controls required by ISO 27001. Ultimately, companies should choose the standards and guidelines that best suit their specific information security needs.
How often do companies need to be recertified for ISO 27001?
Companies need to be recertified for ISO 27001 every three years, or more frequently if there are significant changes to their Information Security Management System (ISMS). The recertification process involves an external audit by a certification body to ensure that the company’s ISMS continues to meet the requirements of the standard. During the three-year certification period, the company is subject to regular surveillance audits to monitor the ongoing effectiveness of their ISMS.
How can ISO 27001 and ISO 27002 benefit companies?
Implementing ISO 27001 and ISO 27002 can benefit companies in several ways. These standards provide a framework for managing information security risks and establishing best practices for the protection of confidential and sensitive data. By complying with these standards, companies can demonstrate their commitment to information security and improve customer trust and confidence. Additionally, implementing ISO 27001 and ISO 27002 can help companies reduce the risk of data breaches and cyberattacks as well as improve overall operational efficiency.

About the Author
NICOLENE KRUGER
Nicolene Kruger, Regional Manager in South Africa, is an experienced Legal Counsel with expertise in compliance and auditing. Her strategic, solution-driven approach aligns legal standards with business objectives, ensuring seamless adherence to regulations.
IS SOC 2 THE SAME AS ISO 27001?
In today's digital landscape, ensuring the safeguarding of client data is paramount for businesses. Adhering to recognized compliance standards is vital to meeting this demand. ISO 27001 vs. SOC 2 represent two prominent benchmarks in the realm of data security with...
WHO NEEDS ISO 27001 CERTIFICATION AND WHY?
The esteemed ISO 27001 security framework is designed to evaluate the effectiveness of an organization's Information Security Management System (ISMS) in safeguarding its data. Obtaining ISO 27001 certification is a practical way for a corporation to demonstrate its...
IS ISO 27001 RISK ASSESSMENT VITAL FOR SECURITY MEASURES?
The ISO 27001 standard provides a framework for information security, highlighting the importance of a thorough risk assessment procedure. Organizations use the methodical and complex ISO 27001 risk assessment process to identify and assess information security...




