In 2024, organizations will be increasingly focused on ensuring robust data security and privacy practices. As the threat landscape evolves, adhering to recognized standards such as SOC 2 (System and Organization Controls 2) becomes crucial. SOC 2 compliance demonstrates an organization’s commitment to safeguarding sensitive information, maintaining the availability of systems, and ensuring the integrity of data.
To achieve the SOC 2 checklist, organizations must meet a set of predefined criteria across five trust service categories: security, availability, processing integrity, confidentiality, and privacy. This checklist serves as a comprehensive guide to help organizations assess and address their compliance requirements, ensuring they meet the stringent SOC 2 standards and instilling confidence in their clients and stakeholders. By following this SOC 2 checklist, organizations can bolster their security posture and establish themselves as trustworthy custodians of data in today’s digital landscape.
WHAT IS SOC 2?
The American Institute of Certified Public Accountants (AICPA) created the SOC 2 set of standards, which focus on the security, availability, processing integrity, confidentiality, and privacy of information systems. A company’s dedication to protecting the privacy of its customers’ data and making sure that its systems and data are secure can be seen by looking for SOC 2 compliance. Organizations will benefit from this checklist’s explanation of SOC 2 compliance certification and its plan for achieving it.
Independent auditors that conduct SOC 2 exams compare an organization’s systems and controls to the Trust Services Criteria (TSC) established by the AICPA. The TSC is a set of rules and standards that are used to determine whether a company has enough security, availability, processing integrity, confidentiality, and privacy controls in place for its systems and data.
There are Type 1 and Type 2 SOC 2 reports. While Type 2 reports assess an organization’s controls over a period of time, usually six to twelve months, Type 1 reports offer a review of an organization’s controls at a particular point in time.
Companies are increasingly using technology for maintaining and handling sensitive data, rendering SOC 2 compliance certification more and more essential. Organizations can gain a competitive edge in the market and boost customer confidence and trust by achieving SOC 2 compliance.
WHY IS SOC 2 IMPORTANT?
Organizations must maintain strict security procedures to guard against potential dangers in this modern age where data breaches and security events are on the rise. SOC 2 compliance is a framework that businesses can use to guarantee the security of their systems and data, as well as the privacy of their consumers.
The significance of SOC 2 lies in its role as an auditing framework that assesses a service organization’s safeguards for securing client data. It instills confidence in customers and stakeholders, affirming the implementation and upkeep of dependable information security measures. For companies handling sensitive data, like financial or health information, SOC 2 compliance is often imperative. By adhering to SOC 2 requirements, these businesses not only showcase their commitment to data security but also proactively avoid potential pitfalls. Assisting organizations in identifying and addressing vulnerabilities in their data security measures can effectively mitigate the likelihood of data breaches and other security incidents, fortifying their overall security posture and safeguarding valuable information.
SOC 2 COMPLIANCE PLAN CHECKLIST
A thorough SOC 2 checklist for 2024 is provided below, outlining all the procedures that businesses must follow to achieve compliance. The following are frequently found in a SOC 2 checklist:
1. Understand the SOC 2 Framework:
Knowing the SOC 2 Framework is important since it describes the requirements that enterprises must complete in order to be in compliance. Organizations should evaluate the SOC 2 criteria and be aware of the particular standards that apply to their sector and line of business.
2. Conduct a Readiness Assessment:
To find any holes in their present data security measures, enterprises should conduct a readiness assessment before pursuing SOC 2 compliance. Organizations can use this assessment to better understand the range of their compliance efforts and set priorities for those efforts.
3. Create a SOC 2 policy:
A SOC 2 policy emphasizes a company’s commitment to data security and details the precise measures it has in place to safeguard consumer data. This policy should be constantly reviewed and updated and should adhere to the SOC 2 requirements.
4. Implement Data Security Controls:
Businesses should put in place data security measures that satisfy SOC 2 standards. Network security, access restrictions, encryption, incident response, and disaster recovery are a few examples of these measures. It is crucial to put controls in place that are suitable for the organization’s particular industry and services.
5. Conduct internal audits:
To evaluate their data security measures and find any gaps or flaws, organizations should conduct internal audits. These audits must be carried out on a regular basis and documented for future use.
6. Engage an Independent Auditor:
Organizations must hire an independent auditor to evaluate their data security measures in order to achieve SOC 2 compliance. This auditor will look at the organization’s policies, practices, and controls to see if they meet the SOC 2 requirements.
7. Address any Issues Found:
If the independent auditor finds any problems or holes in the company’s data security procedures, the organization must close these holes or problems and show that it has put in place reliable safeguards to reduce risks.
8. Get a SOC 2 Report:
The organization will get a SOC 2 report after the independent auditor has finished the evaluation. A description of the organization’s data security measures, the auditor’s assessment of their efficacy, and any issues or vulnerabilities found are all included in this report’s summary of the auditor’s conclusions.
9. Improving data security controls:
Maintain and enhance data security measures because achieving SOC 2 compliance requires ongoing effort. To stay compliant, organizations must maintain and constantly enhance their data security controls. Performing routine internal audits, revising rules and processes, and keeping an eye out for new threats and vulnerabilities are a few examples of how to do this.

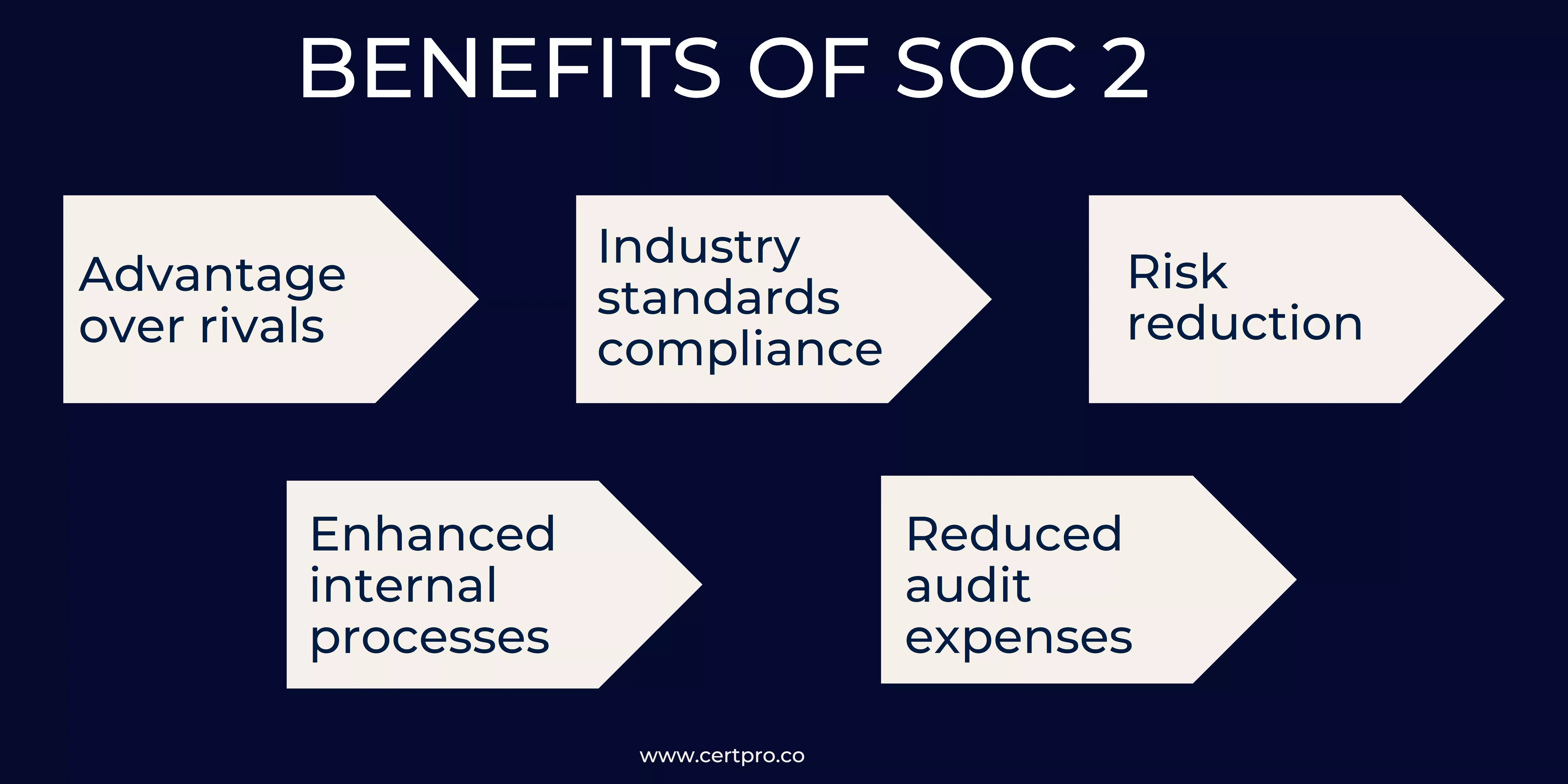
BENEFITS OF SOC 2
Organizations can gain from achieving SOC 2 compliance in a number of ways, including:
- Advantage over rivals: Companies that have attained SOC 2 compliance can set themselves apart from rivals by showcasing their dedication to security and privacy.
- Industry standards compliance: Many firms are required to adhere to particular industry standards, and SOC 2 compliance can assist organizations in doing so.
- Risk reduction: Organizations can reduce the risk of security breaches and other events that could negatively affect their operations by putting in place the measures needed for SOC 2 compliance.
- Enhanced internal processes: In order to achieve SOC 2 compliance, companies must create and put into place policies and practices that address the security, availability, processing integrity, confidentiality, and privacy of information systems. These rules and regulations help streamline internal operations and increase overall business effectiveness.
- Reduced audit expenses: SOC 2 compliance offers independent confirmation of a company’s adherence to legal requirements and industry norms, which can lower audit costs.
OBTAIN SOC 2 COMPLIANCE ASSISTANCE FROM A REPUTABLE AUDITOR CONSULTANCY
A company that specializes in assisting businesses with SOC 2 compliance is called CertPro. To assist businesses in determining any areas where they may fall short of SOC 2 criteria, they offer a variety of services, including risk assessments, gap analysis, and SOC 2 readiness assessments. To maintain SOC 2 compliance, CertPro may also help with the creation of policies and procedures, employee training, continual monitoring, and reporting.
Overall, obtaining SOC 2 compliance can be a challenging process, but with the assistance of a dependable partner like CertPro, businesses can simplify the procedure and make sure they are fulfilling all standards for safeguarding consumer data and upholding compliance. Companies may engage with CertPro and feel secure knowing that their systems are safe and secure.
WHY SHOULD A SOC 2 CHECKLIST BE IMPLEMENTED?
Using a SOC 2 checklist shows your commitment to security and gives consumers trust that their data is protected. It also expedites the audit readiness process and guarantees comprehensive coverage. Organizations are forced to define and record policies, procedures, and controls by the SOC 2 audit.
In addition to greatly lowering business risks, this thorough documentation improves vendor management practices, which frequently results in more streamlined operational efficiency. Adopting these fundamental procedures fortifies security measures and improves overall resilience in the ever-changing data management ecosystem, making it the cornerstone of strong corporate practices.
THE CHALLENGES OF IMPLEMENTING THE SOC 2 COMPLIANCE CHECKLIST
SOC 2 compliance is a significant undertaking loaded with difficulties. The time-consuming work of precisely documenting controls, policies, and procedures to fulfill SOC 2 standards, which requires significant time and effort, is a significant barrier. Costs for essential changes to infrastructure or systems to meet compliance criteria may be incurred.
The journey continues even after compliance. Maintaining SOC 2 compliance necessitates continuing internal control audits, necessitating a consistent commitment. Despite the daunting hurdles, the goal is crucial for firms that manage critical consumer data, serving as a testament to reliability and unwavering security promises.
FAQ
Is it possible for a business to achieve SOC 2 compliance without engaging an outside auditor?
No, without the help of a third-party auditor, a corporation cannot achieve SOC 2 compliance. An independent CPA firm that is authorized to conduct SOC 2 audits must carry out the audit.
How frequently should a business get a SOC 2 audit?
To maintain compliance, businesses should go through a SOC 2 audit at least once a year. However, depending on the size, complexity, and industry laws of the organization, the frequency of audits may change.
What occurs if a business fails a SOC 2 audit?
A corporation may need to alter its policies, practices, and controls if it receives a SOC 2 audit failure in order to correct any shortcomings. To make sure that any flaws found during the audit have been rectified, the organization can also be forced to undertake further audits or assessments.
What distinguishes a Type I SOC 2 report from a Type II SOC 2 report?
A Type II SOC 2 report reviews both the design and effectiveness of the controls over a given period, often six months to a year, as opposed to a Type I SOC 2 report, which assesses the controls’ design at a particular point in time.
soc 2 requirements checklist
The SOC 2 requirements checklist is crucial for ensuring systematic adherence to security standards. It provides a structured framework for implementing controls, policies, and procedures, fostering compliance, and fortifying data protection measures.

About the Author
GANESH S
Ganesh S, an expert in writing content on compliance, auditing, and cybersecurity, holds a Bachelor of Arts (BA) in Journalism and Mass Communication. With a keen eye for detail and a knack for clear communication, Ganesh excels in producing informative and engaging content in the fields of compliance, auditing, and cybersecurity, with particular expertise in ISO 27001, GDPR, SOC 2, HIPAA, and CE Mark.
HOW CAN STARTUPS ATTAIN SOC 2 COMPLIANCE IN 2024?
Trust is crucial for startups to do well in today's digital world. It's vital for establishing credibility with clients, especially in a data-driven environment where privacy is the main component. Therefore, getting a SOC 2 compliance report is crucial to building...
SOC TOOLS: How They Impact On Security Aspect Of The Organization
The changing cybersecurity landscape increases the importance of Security Operations Center (SOC) tools. Hence, it is essential for strengthening digital defenses and protecting against cyberattacks. SOC tools help security teams detect, monitor, and prevent security...
WHAT IS SOC FOR CYBERSECURITY?
In today's fast-paced digital landscape, ensuring robust cybersecurity measures is imperative for organizations aiming to protect sensitive data and maintain stakeholder trust. The American Institute of CPAs (AICPA) crafted the SOC for cybersecurity reporting...




