SOC-2 Type I vs Type II reports play a critical role in evaluating the security posture of organizations that provide services to other companies. With the increasing adoption of cloud-based services and outsourcing, it has become crucial to have a reliable security framework in place. SOC-2 is an auditing standard that certifies the security and privacy of systems at such organizations. SOC-2 reports offer crucial information to clients and stakeholders to assess an organization’s security and compliance. However, there are differences between SOC-2 Type I and Type II reports, with the latter providing more comprehensive and extensive testing of an organization’s controls over a longer period.
SOC-2 reports are classified into two distinct types: SOC-2 Type I and Type II. In this blog post, we will discuss the differences between SOC-2 Type I vs Type II, their benefits, and how they can be used to secure your organization’s systems.
soc-2 compliance
- Demonstrate their commitment to data security and sequestration.
- An impartial third-party CPA conducts the inspection, evaluates the association’s controls in relation to the Trust Services Criteria, and then provides a report on their efficacy.
- By achieving SOC-2 compliance, service associations can demonstrate to their guests and stakeholders that they’re committed to guarding sensitive data and have enforced acceptable controls to alleviate the pitfalls connected to security issues such as data leaks, cyberattacks, and others. Achieving SOC-2 compliance can help service associations build trust with their guests and stakeholders and separate themselves in a crowded market.
SOC-2 Type 1
A SOC-2 Type I report evaluates the design of a company’s controls to ensure they are suitably designed to meet the relevant trust service principles. The five fundamental principles that SOC-2 reports encompass are security, availability, processing integrity, confidentiality, and privacy. The report is a snapshot of the controls in place at a specific point in time and was conducted at a specific date or range of dates.
An independent auditor performs the SOC-2 Type I audit and confirms that the organization’s controls are created to adhere to the trust service principles. The report provides assurance to stakeholders that the company has established controls to meet the trust principles, and it is a crucial first step in obtaining SOC-2 certification.
One key limitation of the SOC-2 Type I report is that it does not assess the operating effectiveness of the controls. Therefore, it is possible that a control that is designed to meet the trust service principles may not be functioning effectively, resulting in a potential gap in security.
SOC-2 Type I Report
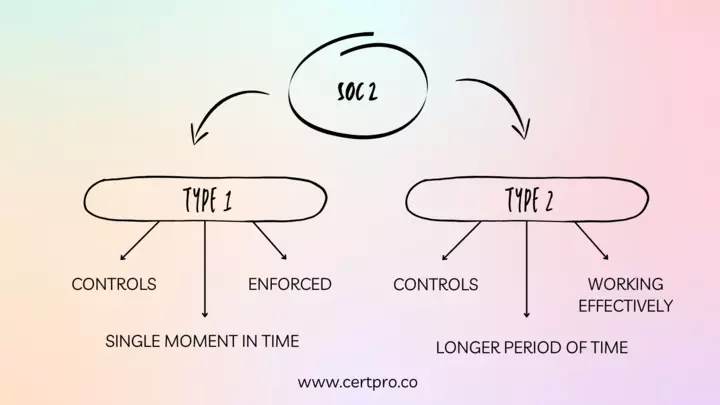
A SOC-2 Type I report evaluates a service organization’s controls based on the Trust Services Criteria (TSCs) at a specific point in time. This report provides an independent auditor’s perspective on the design and implementation of the organization’s controls and their ability to meet the TSCs.
The auditor reviews whether the controls have been adequately designed and implemented to meet the TSCs in a SOC-2 Type I report. This report offers an unbiased assessment of the organization’s controls and can be used to demonstrate to stakeholders that the organization has established and implemented effective controls to protect sensitive data and ensure information confidentiality, integrity, and availability. It is important to note that a SOC-2 Type I report does not evaluate the operational performance of the controls over time. This is evaluated in a SOC-2 Type II report, which covers at least six months and assesses the quality of controls during that period.
A SOC-2 Type II report goes beyond the design of controls to evaluate their operating effectiveness over a specified period, typically six months or more. The Type II audit includes all the principles evaluated in a Type I report and assesses the controls’ effectiveness in achieving the objectives set forth in the trust principles. During a SOC-2 Type II audit, an independent auditor performs a series of tests to determine if the controls are operating effectively. The audit provides an assessment of the overall effectiveness of the controls, identifies potential gaps in security, and helps organizations implement corrective actions to address any issues. The SOC-2 Type II report provides more comprehensive information about the organization’s controls than the SOC-2 Type I report. It provides stakeholders with assurance that the controls are operating effectively to meet the trust principles and gives clients the confidence to use the organization’s services.
SOC-2 Type II Report
SOC-2 Type II reports assess a service organization’s controls based on the Trust Services Criteria (TSCs) over a specific period of time, often a minimum of six months. This report provides an independent auditor’s view on the design and operational effectiveness of the organization’s controls to meet the TSCs.
The auditor reviews whether the controls have been appropriately designed and effectively operated to meet the TSCs during the designated period in the SOC-2 Type II report. This report provides a comprehensive evaluation of the organization’s controls and can be used to demonstrate to stakeholders that the organization has established and implemented effective controls to protect sensitive data and maintain the confidentiality, integrity, and availability of information over time.x
SOC-2 Type II reports are more stringent than Type I reports as they evaluate the effectiveness of controls over time rather than just their design and implementation. This increases the value of SOC-2 Type II reports for enterprises that handle sensitive data and need to assure their stakeholders that they have implemented and maintained appropriate controls to secure that data.
Benefits of SOC-2 Type I and Type II Reports
SOC-2 reports offer several benefits for organizations and their clients, including:
- Improved security and compliance: SOC-2 reports help organizations identify and implement controls to meet the trust principles. By doing so, they can improve their security posture and ensure compliance with industry and regulatory standards.
- Competitive advantage: SOC-2 reports are increasingly becoming a requirement for doing business with enterprise clients. Obtaining SOC-2 certification demonstrates an organization’s commitment to security and can provide a competitive advantage over competitors that do not have the certification.
- Increased transparency: SOC-2 reports provide clients with transparency about the organization’s security and privacy controls. The reports help clients understand the measures the organization has put in place to protect their data and assess the organization’s compliance with industry and regulatory standards.
SOC-2 Type I and Type II reports are essential for organizations that handle sensitive data and want to demonstrate their commitment to security and privacy. Understanding the difference between these two types of reports can help organizations choose the right type based on their needs and goals.
Steps towards obtaining a SOC-2 Type 1 or Type 2 certification:
- Identify the relevant Trust Services Criteria (TSC): Determine which of the five TSCs (security, availability, processing integrity, confidentiality, and privacy) are applicable to your organization and the services you provide.
- Engage an auditor: Choose a licensed CPA firm to conduct the SOC-2 audit. It is recommended to select an auditor who is experienced with SOC-2 certifications in your industry.
- Prepare for the audit: Develop and implement controls that align with the selected TSCs. The organization must also ensure that documentation is accurate, up-to-date, and readily available for the auditor’s review.
- Conduct a readiness assessment: Conduct a gap analysis to identify any areas where the organization’s controls are deficient or require improvement before the SOC-2 audit.
- Perform the SOC-2 audit: The auditor will conduct an assessment of the organization’s controls to determine their design adequacy and implementation effectiveness. The audit process may take several weeks to complete.
- Receive the SOC-2 report: If the organization passes the audit, the auditor will issue a SOC-2 report, which can be provided to customers, partners, and other stakeholders as evidence of the organization’s commitment to security and data privacy.
- Maintain compliance: To maintain SOC-2 compliance, the organization must continue to monitor and improve its controls to ensure they are effective in mitigating risks and protecting data. Annual SOC-2 audits are recommended to maintain compliance.
It is important to note that the process of obtaining a SOC-2 certification can vary depending on the organization’s size, industry, and specific requirements. Therefore, it is recommended to consult with an experienced auditor and follow best practices to achieve a successful SOC-2 certification.
How Certpro helps organizations become SOC-2 Type I and Type II compliant
At Certpro, we understand that achieving SOC-2 compliance can be a complex and time-consuming process. That’s why we offer a range of services designed to help organizations become SOC-2 Type I and Type II compliant efficiently and effectively.
Our SOC-2 compliance services include:
Gap Analysis: We conduct a thorough assessment of your organization’s existing controls to identify any gaps in meeting the SOC-2 requirements.
Remediation: We help you address the gaps identified in the gap analysis by developing and implementing effective controls to meet the SOC-2 requirements.
SOC-2 Readiness Assessment: We evaluate your organization’s readiness for SOC-2 Type I and Type II certification and provide recommendations for improvement.
SOC-2 Type I and Type II Certification: We provide independent SOC-2 Type I and Type II audit services, which are performed by our team of experienced auditors.
Our team has extensive experience in SOC-2 compliance and can provide customized solutions tailored to your organization’s specific needs. We use a proven methodology to ensure that our clients achieve SOC-2 compliance efficiently and effectively.
By working with Certpro, organizations can streamline the SOC-2 compliance process, reduce the risk of non-compliance, and demonstrate to their stakeholders that they have implemented effective controls to protect sensitive data and maintain the confidentiality, integrity, and availability of information.

About the Author
SUBBAIAH KU
Subbaiah Ku is the Regional Director for CertPro in Oman, bringing a wealth of expertise in process and system auditing. As a seasoned lead assessor, Subbaiah is dedicated to ensuring the highest standards in compliance and security. His unique blend of technical acumen, rooted in Mechanical Engineering, is complemented by a diverse range of certifications and extensive training.
HOW CAN STARTUPS ATTAIN SOC 2 COMPLIANCE IN 2024?
Trust is crucial for startups to do well in today's digital world. It's vital for establishing credibility with clients, especially in a data-driven environment where privacy is the main component. Therefore, getting a SOC 2 compliance report is crucial to building...
SOC TOOLS: How They Impact On Security Aspect Of The Organization
The changing cybersecurity landscape increases the importance of Security Operations Center (SOC) tools. Hence, it is essential for strengthening digital defenses and protecting against cyberattacks. SOC tools help security teams detect, monitor, and prevent security...
WHAT IS SOC FOR CYBERSECURITY?
In today's fast-paced digital landscape, ensuring robust cybersecurity measures is imperative for organizations aiming to protect sensitive data and maintain stakeholder trust. The American Institute of CPAs (AICPA) crafted the SOC for cybersecurity reporting...




