System and Organization Controls (SOC) 2 is a comprehensive assessment used to confirm that an organization satisfies the standards set out by the American Institute of Certified Public Accountants (AICPA). This assessment looks at the Common Criteria, which cover a wide range of system controls meant to make sure the company runs using the best cybersecurity practices possible. It becomes essential to have a strong business continuity plan to support these procedures and ensure the ongoing functionality of operations.
An organization’s adherence to AICPA criteria and its commitment to maintaining strict cybersecurity standards are both validated by the SOC 2 test. The common criteria included in this analysis include a wide range of system control components, highlighting the importance of a holistic cybersecurity strategy. It emphasizes how crucial it is to implement industry-leading procedures to protect sensitive data and uphold the integrity of business operations.
The creation and implementation of a business continuity plan is a crucial tactic in the field of cybersecurity to guarantee best practices. By reducing potential hazards and business operations disruptions, this plan serves as a safety net. When implemented, it greatly increases an organization’s overall resilience by enabling it to handle unforeseen obstacles with ease. When included in an organization’s structure, the Business Continuity and Disaster Recovery Plan not only satisfies the standards specified by the SOC 2 assessment but also acts as a preventative step against possible risks. Organizations may inspire trust in stakeholders and show their commitment to upholding a safe and resilient operating environment by highlighting the significance of readiness and continuity planning.
To sum up, the SOC 2 assessment and the execution of a business continuity and disaster recovery plan are essential elements of an all-encompassing cybersecurity approach. These actions highlight the necessity of a proactive approach to business continuity strategies by confirming an organization’s dedication to cybersecurity best practices and strengthening its resilience to unanticipated obstacles.
WHAT IS A BUSINESS CONTINUITY PLAN?
A business continuity plan, or BCP, is an essential document that describes how a company will handle crises or significant disruptions and recover. Its main goal is to make it possible for the company to minimize downtime and continue vital operations both during and after such incidents. Upholding customer service, guaranteeing uninterrupted operations, and giving priority to safety precautions are among the major responsibilities of a BCP. A well-designed business continuity strategy. is only as good as its capacity to reduce the financial and reputational damage that unexpected catastrophes might cause. A BCP should be regularly reviewed and updated to reflect organizational changes, such as the addition of new facilities, procedures, or technology. This is because a BCP is dynamic. This flexibility guarantees that the business continuity and disaster recovery plan will continue to be relevant and effective in preserving the resilience of the organization.
DOES SOC 2 COVER BUSINESS CONTINUITY?
A business continuity and disaster recovery plan is included in the documentation that a SOC 2 auditor reviews; this is an important component in addition to the audit of your systems and security measures. The results of this extensive assessment show how well the chosen Trust Services Criteria (TSC) are being adhered to. The business continuity strategy is especially important when availability is included as a TSC in your SOC 2 audit.
The availability controls in SOC 2 place a high priority on reducing downtime and highlight the need for a thorough risk assessment. The auditor will likely examine if your business has recognized and developed strategies to mitigate “man-made” risks like theft and cyberattacks as well as “environmental” hazards like hurricanes, tornadoes, and wildfires.
In addition, the SOC 2 auditor will evaluate how well your business continuity strategy responds to unanticipated circumstances that affect system capacity and availability, such as a pandemic. Verifying whether your business continuity strategy has been tested in the last year is a crucial component of this assessment, as it guarantees the plan’s continued efficacy. As a result, a SOC 2 audit’s thorough scope must include an analysis of a business continuity strategy to fully address the range of risks to system availability and capacity.
HOW DOES SOC 2 ENSURE BUSINESS CONTINUITY?
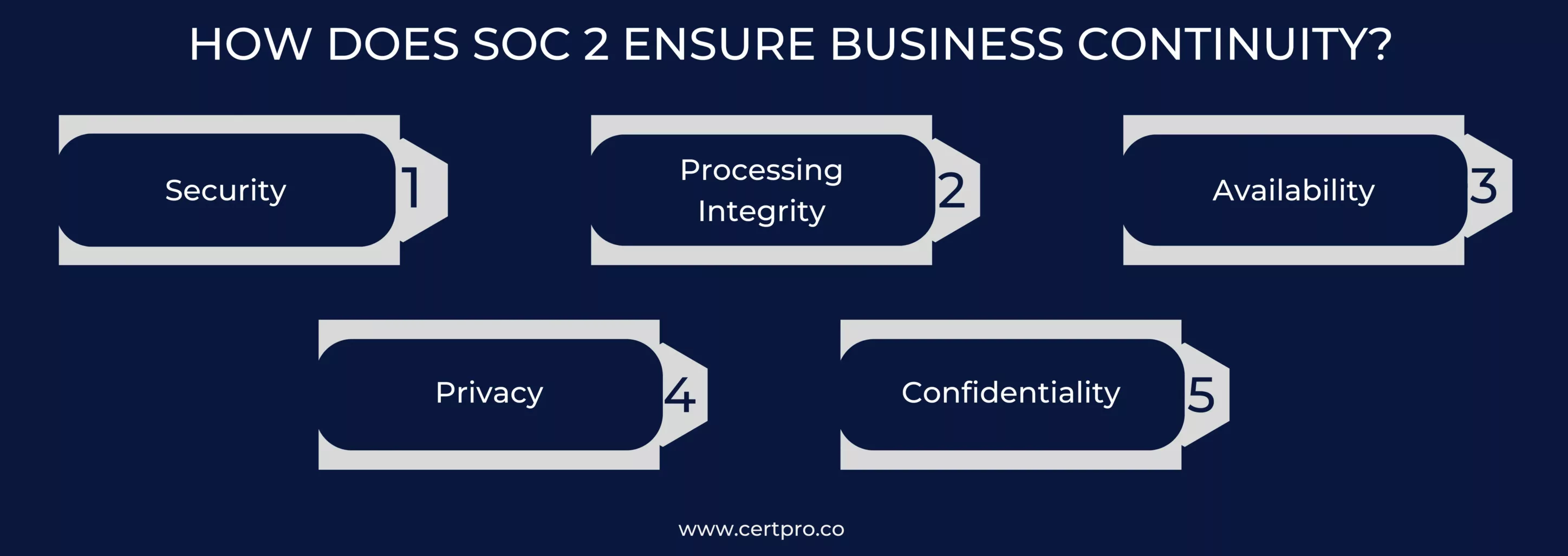
Cybersecurity events frequently result in business disruptions. The SOC acts as an audit tool to guarantee data security, protecting your business and its clients from possible security breaches and harm to their reputations. SOC 2 evaluates five standards of trust:
- Security: How well-defended against unwanted access is your network?
- Processing Integrity: Does your network process data in an accurate, timely, authorized, and complete manner, fulfilling its intended purpose?
- Availability: Are clients able to use the network as scheduled?
- Privacy: Does the network adhere to the commonly accepted privacy rules of the AICPA while handling private data?
- Confidentiality: Is private information sufficiently protected?
Customization is a built-in component of SOC 2, enabling businesses to modify controls and procedures in accordance with the principles that guide the auditing procedure. This adaptability gives every business the ability to identify and rank issues in accordance with their unique requirements.
SOC 2 compliance is proof that the obligation to protect data has been met. For instance, banks have a duty to protect customer personal identity information, such as social security numbers. Breaching the security measures intended to protect such information could lead to serious financial and reputational consequences.
Robust data protection is built on top of SOC 2 compliance. Less serious breaches affect SOC 2-compliant organizations than non-compliant ones, which minimizes interruptions in the case of a security incident. Heavy fines for noncompliance might potentially bankrupt a company, particularly if they are applied following a security breach.
SOC 2, which has facilities for continuous assessments, is a useful instrument for preserving security and privacy. To maintain your organization’s SOC 2 accreditation, you must demonstrate adherence to necessary standards by consistently following pertinent procedures.
THE IMPORTANCE OF BUSINESS CONTINUITY PLAN
The importance of business continuity plan cannot be overstated, as it is crucial for safeguarding businesses. Without a comprehensive strategy for emergencies, organizations risk significant financial setbacks, damage to brand reputation, and a decline in consumer trust. Establishing and implementing a plan for business continuity is vital for resilience and sustained success, highlighting its importance in mitigating risks and ensuring long-term stability.
- Ensuring Stakeholder Safety: It is vital to ensure the safety of stakeholders, customers, and employees. The plan for business continuity plays a crucial role in this regard by providing clear guidelines for handling unanticipated emergencies.
- Minimizing Downtime and Sustaining Operations: In order to minimize downtime during emergencies, a well-crafted plan for business continuity is crucial. It makes it possible for businesses to smoothly continue vital operations, guaranteeing resilience and continuity.
- Protecting Organizational Reputation: The plan’s capacity to swiftly and effectively respond to catastrophes safeguards the organization’s reputation. In the view of partners, clients, and the larger community, this is especially important.
- Mitigating Financial Impact: The goal of the plan is to reduce the financial impact of emergencies. The organization can lessen the financial losses brought on by disruptions by taking preventive steps and responding strategically as specified in the strategy.
In conclusion, the importance of business continuity plan cannot be overstated. A well-crafted plan not only prioritizes stakeholder safety and ensures seamless operations but also safeguards the organization’s financial stability and reputation in the face of unforeseen calamities. Recognizing the importance of business continuity plan is vital for any business aiming to thrive in a dynamic and unpredictable environment.
BUSINESS CONTINUITY PLAN COMPONENTS
An effective business continuity strategy needs to include its key elements. Among them are essential components that guarantee the organization’s resilience against disturbances. To protect business operations, it is essential to incorporate thorough strategies, risk assessments, and crisis management protocols. A well-structured plan includes critical business continuity plan components, which promote readiness and reduce potential interruptions:
1. Analysis of Business Impact: Conduct a business impact analysis (BIA) to kickstart the creation of a plan for business continuity. Analyze possible disruptions to critical operations, differentiating between procedures that are necessary for the existence of the company and those that, in the event of an interruption, have manageable repercussions.
2. Risk Evaluation: Once important business processes have been identified, the next stage is to assess the risks that could interfere with them. This includes pandemics, cyberattacks, power disruptions, and natural calamities. Setting priorities for important procedures and creating a plan to mitigate risks are made possible by carrying out a thorough risk assessment.
3. Strategy for Business Continuity: The actions that will be taken to maintain the organization’s operations in the event of an interruption are outlined in the business continuity strategy. The plan must be customized to meet the unique requirements of the company and cover every facet of the business continuity strategy, including people, buildings, procedures, and technology.
4. Recuperation Group: The recuperation team—which consists of key members from multiple organizational departments—is responsible for carrying out the plan for business continuity. The plan must be reviewed at regular team meetings in order to identify any necessary revisions and guarantee the strategy’s ongoing efficacy.
5. Training: Ensuring that each member of the business recovery team is well trained in their assigned duties and responsibilities is crucial. Every employee should also complete training so that they are knowledgeable about what to do in the event of an emergency.
6. Actions for Business Continuity: In order to evaluate and identify any flaws in the business continuity strategy, business continuity exercises simulate disruptions to corporate operations. Maintaining the efficacy and readiness of the strategy requires regular exercises that can be adjusted to organizational changes.
7. Communication: During disruptions, effective communication is essential for informing stakeholders, customers, and staff. A comprehensive plan for business continuity needs to include a communication strategy that identifies the people in charge of reaching out to various groups. The plan should also include communication channels for sharing important information, such as social media, text messaging, and email.
8. Backup Sites and Material Resources: It can be necessary to relocate business processes in the event of a disruption. A complete plan for business continuity ought to include a list of backup sites along with pertinent contact information. It should also list the tangible resources—such as computer hardware—necessary to maintain operations at the backup site.
9. Regular Evaluation and Suggestions: It is essential to regularly assess the plan for business continuity and make any necessary revisions. A comprehensive plan review is necessary after big organizational changes like mergers or acquisitions. Getting business continuity experts involved is beneficial because they can evaluate and improve the strategy and make suggestions for enhancements.
10. Technology: Technology is essential to business continuity and should be included in the plan. The strategy should include backup data, emergency power, and redundant systems, among other precautions, to guarantee that critical systems are still accessible in the event of an interruption. To keep up With the rapidly changing technological landscape, organizations must regularly upgrade their systems to reflect changes in their operations and teach their staff about crucial technology usage.
FAQ
How does SOC 2 accreditation ensure business continuity in organizations?
SOC 2 accreditation ensures business continuity by evaluating an organization’s adherence to strict cybersecurity controls, including the implementation of a robust business continuity and disaster recovery plan. The assessment considers the Common Criteria and Trust Services Criteria, emphasizing the importance of a holistic approach to cybersecurity and readiness for potential disruptions.
What role does a business continuity and disaster recovery plan play in SOC 2 compliance?
SOC 2 auditors review documentation, and a business continuity and disaster recovery plan constitutes a crucial component of SOC 2 compliance. The plan supports the Trust Services Criteria, particularly when availability is a key consideration, demonstrating an organization’s commitment to reducing downtime and addressing risks like cyberattacks and environmental hazards.
How does SOC 2 address the availability of systems and the need for a business continuity strategy?
SOC 2 places a high priority on system availability through its controls, emphasizing the importance of a business continuity strategy. The auditor assesses an organization’s response to unanticipated circumstances, ensuring that the business continuity and disaster recovery plan effectively address risks to system availability, including those arising from cyber threats and natural disasters.
In what ways does SOC 2 compliance contribute to overall cybersecurity and data protection?
SOC 2 compliance contributes to overall cybersecurity and data protection by evaluating an organization’s adherence to security, processing integrity, availability, privacy, and confidentiality standards. This ensures that sensitive data is adequately protected, minimizing the risk of security breaches and reinforcing the organization’s commitment to data security.
What are the key business continuity plan components?
A business continuity and disaster recovery plan comprises several essential components to ensure an organization’s resilience during disruptions. These include an analysis of business impact, risk evaluation, a strategy for business continuity, a designated recovery team, regular training and exercises for continuity, effective communication plans, backup sites, and material resources, consistent evaluation, and the incorporation of technology to support critical systems.

About the Author
NICOLENE KRUGER
Nicolene Kruger, Regional Manager in South Africa, is an experienced Legal Counsel with expertise in compliance and auditing. Her strategic, solution-driven approach aligns legal standards with business objectives, ensuring seamless adherence to regulations.
HOW CAN STARTUPS ATTAIN SOC 2 COMPLIANCE IN 2024?
Trust is crucial for startups to do well in today's digital world. It's vital for establishing credibility with clients, especially in a data-driven environment where privacy is the main component. Therefore, getting a SOC 2 compliance report is crucial to building...
SOC TOOLS: How They Impact On Security Aspect Of The Organization
The changing cybersecurity landscape increases the importance of Security Operations Center (SOC) tools. Hence, it is essential for strengthening digital defenses and protecting against cyberattacks. SOC tools help security teams detect, monitor, and prevent security...
WHAT IS SOC FOR CYBERSECURITY?
In today's fast-paced digital landscape, ensuring robust cybersecurity measures is imperative for organizations aiming to protect sensitive data and maintain stakeholder trust. The American Institute of CPAs (AICPA) crafted the SOC for cybersecurity reporting...




