The Health Insurance Portability and Accountability Act stands as a cornerstone of data protection and privacy within the healthcare industry, ensuring the security of patients’ sensitive information. Central to HIPAA risk assessment compliance is the imperative task of conducting a comprehensive risk assessment. This strategic process enables healthcare organizations to systematically identify potential vulnerabilities, assess risks, and develop targeted safeguards to fortify the confidentiality, integrity, and availability of electronic protected health information (ePHI).
The primary goal of a HIPAA risk assessment is to proactively identify and address areas of potential weakness in an organization’s security infrastructure that could compromise the sensitive data it handles. By conducting this assessment, healthcare entities can meticulously evaluate their existing security measures, pinpoint areas of concern, and formulate effective strategies to minimize risks. With the ever-evolving landscape of cybersecurity threats and regulatory changes, a thorough understanding of this becomes paramount in establishing a robust foundation for continued compliance and data protection.
In this article, we will delve into the intricacies of conducting a risk assessment under the Health Insurance Portability and Accountability Act, outlining each step of the process to equip healthcare professionals and organizations with the knowledge and tools needed to navigate this critical aspect of safeguarding patient data and upholding the principles of Health Insurance Portability and Accountability Act compliance.
WHAT IS A HIPAA RISK ASSESSMENT?
The Health Insurance Portability and Accountability Act mandates stringent privacy and security measures for safeguarding individuals’ protected health information (PHI) within the healthcare industry. It is a comprehensive evaluation that healthcare organizations and their business associates must undergo to identify, manage, and mitigate potential risks to the confidentiality, integrity, and availability of PHI.
The detected risks and vulnerabilities may have an influence on the HIPAA security risk assessment and integrity of your environment’s electronic PHI (ePHI). As a result, in order to comply with and maintain compliance with the Health Insurance Portability and Accountability Act, covered entities (healthcare providers, health plans, and healthcare clearinghouses) and business associates (service providers) (and suppliers of covered entities that use or disclose PHI) must conduct risk assessments on a regular basis.
It is recommended to undertake risk assessments on an annual basis or if new technology or substantial changes, such as improvements to your health information technology systems and processes, are introduced.
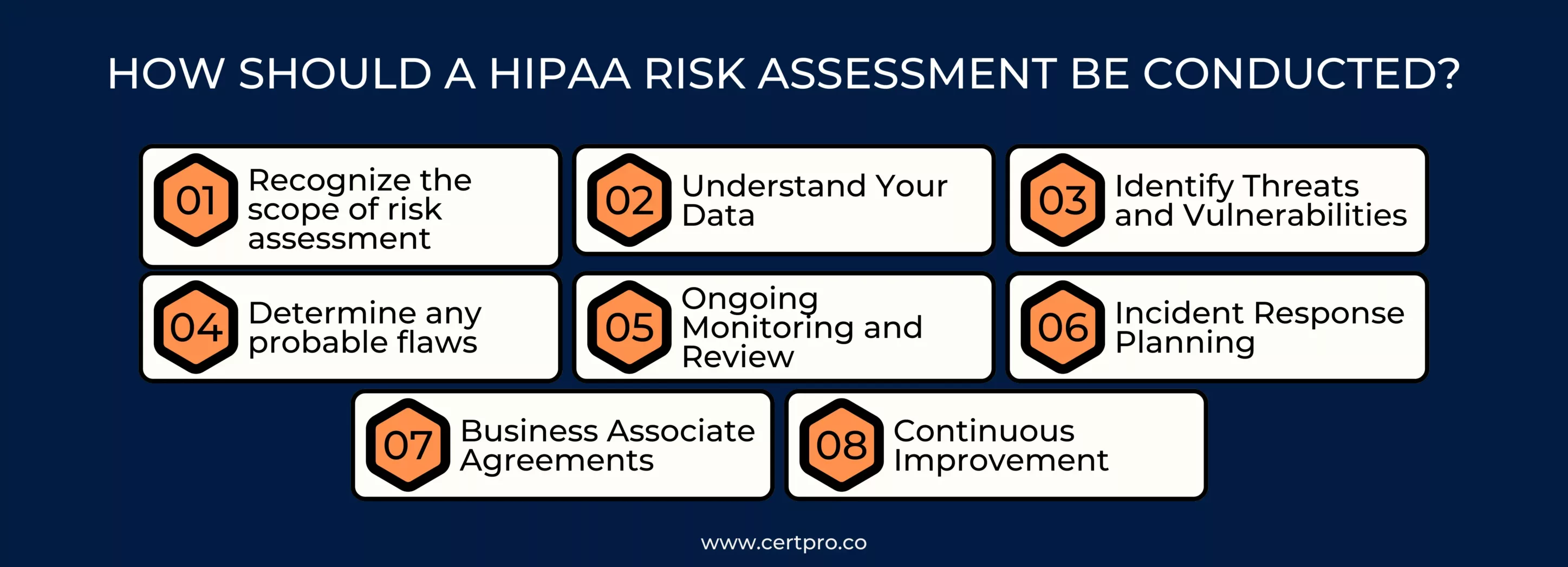
HOW SHOULD A HIPAA RISK ASSESSMENT BE CONDUCTED?
The HIPAA Security Risk Assessment does not specify a mechanism for undertaking a risk analysis. Instead, corporations regularly rely on standards such as NIST 800-30 for Health Insurance Portability and Accountability Act compliance criteria. NIST SP 800-30 establishes a standard risk assessment methodology for assessing the effectiveness of HIPAA security risk assessment controls in information systems.
This step-by-step risk assessment guide will help you through the process:
1. Recognize the scope of risk assessment: This includes e-PHI on all forms of electronic media and portable electronic media. Your organization’s security risk assessment must encompass all e-PHI, regardless of electronic medium or location.
2. Understand Your Data: It must identify the locations in your company where ePHI is stored, received, maintained, or transmitted. To obtain all of the information needed for this, you could analyze the organization’s past and current initiatives.
3. Identify Threats and Vulnerabilities: List potential risks like cyberattacks, unauthorized access, or physical breaches. Identify vulnerabilities that could be exploited, such as weak passwords or outdated software.
4. Determine any probable flaws: Organizations must identify and document vulnerabilities that could lead to a PHI breach. This can be accomplished by examining previous or current projects, conducting interviews with personnel who handle PHI, and analyzing documentation.
5. Ongoing Monitoring and Review: Continuously monitor the effectiveness of HIPAA risk management plan strategies. Regularly review and update the assessment to address new risks, changes in technology, or organizational shifts.
6. Incident Response Planning: Develop an incident response plan outlining steps to take in the event of a data breach or security incident involving PHI.
7. Business Associate Agreements (BAAs): Ensure that third-party vendors and partners handling PHI have appropriate agreements in place that outline their responsibilities for data protection.
8. Continuous Improvement: Regularly assess and refine your risk assessment process to adapt to evolving threats, technologies, and best practices.
By following these steps, healthcare organizations can proactively identify vulnerabilities, enhance PHI security, and ensure compliance with the Health Insurance Portability and Accountability Act.
BENEFITS OF HIPAA RISK ASSESSMENT
Conducting a risk assessment offers several important benefits for healthcare organizations and their business associates. These benefits contribute to improved patient data security, compliance with Health Insurance Portability and Accountability Act regulations, and overall organizational resilience.
Some key advantages of performing a risk assessment are:
1. Enhanced Patient Data Security: This helps identify potential vulnerabilities and threats to protected health information (PHI). By addressing these risks through appropriate safeguards and controls, organizations can significantly enhance the security of patient data, reducing the likelihood of data breaches and unauthorized access.
2. Compliance with HIPAA Regulations: It mandates that covered entities and business associates implement security measures to protect PHI. It ensures that an organization’s security practices align with Health Insurance Portability and Accountability Act requirements, helping to maintain compliance and avoid potential penalties and legal actions.
3. Risk Prioritization and Resource Allocation: Through this, organizations can prioritize risks based on their potential impact and likelihood. This enables them to allocate resources more effectively and efficiently to address high-priority risks that pose the greatest threat to patient data security.
4. Proactive Identification and Mitigation of Risks: This allows organizations to identify vulnerabilities and threats before they lead to actual security incidents. This proactive approach helps prevent data breaches, reducing the financial and reputational consequences associated with them.
5. Customized Security Measures: It helps organizations tailor their security measures to their specific risks and vulnerabilities. This ensures that security investments and efforts are focused on the areas that need the most attention, optimizing the use of resources.
6. Long-Term Sustainability: Regular risk assessments promote continuous improvement in data security practices. As risks evolve and new technologies emerge, organizations can adapt and stay resilient in the face of changing threats.
In summary, a HIPAA risk assessment is a critical tool for protecting patient health information, ensuring regulatory compliance, and fostering a culture of security within healthcare organizations.

TIPS FOR A SUCCESSFUL HIPAA RISK ASSESSMENT
A successful Health Insurance Portability and Accountability Act risk assessment is essential for ensuring the HIPAA security risk assessment and HIPAA privacy risk assessment of protected health information (PHI) in the healthcare industry.
To complete a good risk assessment, keep the following recommendations in mind:
- Determine who will oversee the evaluation.
- Understand that you can do the evaluation in-house or hire a Health Insurance Portability and Accountability Act specialist to do it for you. Outsourcing the evaluation may allow the analytical and planning duties to be completed more quickly.
- Remember the assessment’s purpose. It is not an audit; its goal is to assist you in identifying, prioritizing, and mitigating risks.
- Check that your documentation complies with Health Insurance Portability and Accountability Act requirements. All procedures and policies should be documented, checked for accuracy, and made centrally available.
- Remember that you must repeat the assessment process at least once a year.
- Provide HIPAA compliance training to all employees.
By following these tips, you can conduct a successful risk assessment and enhance the overall security and HIPAA privacy risk assessment of PHI within your organization.
ATTAINING HIPAA COMPLIANCE WITH CERTPRO’S EXPERT RISK ASSESSMENT
Conducting a risk assessment is an indispensable undertaking for healthcare organizations to protect sensitive patient information and ensure compliance with regulatory requirements. In this journey towards comprehensive data protection, partnering with a trusted Health Insurance Portability and Accountability Act compliance expert like CertPro can be invaluable. CertPro’s experienced professionals offer guidance and support throughout the risk assessment process, ensuring healthcare organizations navigate the complexities of compliance with confidence. With CertPro’s expertise, healthcare entities can establish robust data security measures, maintain Health Insurance Portability and Accountability Act compliance, and safeguard patient trust.
FAQ
WHY IS A RISK ASSESSMENT UNDER HIPAA IMPORTANT?
It is crucial to proactively identify and manage risks that could compromise patient data. It ensures compliance, minimizes the risk of data breaches, and safeguards patient privacy.
WHO SHOULD PERFORM A RISK ASSESSMENT OF HIPAA?
Healthcare organizations, including covered entities and business associates, should conduct risk assessments. They are responsible for ensuring PHI security and complying with Health Insurance Portability and Accountability Act rules.
HOW OFTEN SHOULD RISK ASSESSMENT UNDER HIPAA BE DONE?
It should be conducted regularly, especially when there are changes in systems, processes, or regulations. Regular assessments help maintain up-to-date PHI security measures.
WHAT ARE THE POTENTIAL CONSEQUENCES OF NOT PERFORMING A RISK ASSESSMENT UNDER HIPAA?
Failure to do so can lead to data breaches, legal actions, financial penalties, and damage to an organization’s reputation. It also risks non-compliance with Health Insurance Portability and Accountability Act regulations.
WHAT SAFEGUARDS ARE TYPICALLY CONSIDERED IN RISK ASSESSMENT UNDER THE Health Insurance Portability and Accountability Act?
Safeguards may include technical measures (encryption, access controls), administrative controls (policies, staff training), and physical safeguards (facility security) to protect PHI.

About the Author
SHREYAS SHASTHA DRUPADHA
Shreyas Shastha Drupadha, a Senior Business Consultant. Serving as an ISO 27001 Lead Auditor, Shreyas ensures the establishment of robust information security management systems. His expertise also encompasses GDPR, HIPAA, CCPA, and PIPEDA implementation.
HITECH ACT AND ITS IMPACT ON MODERN HEALTHCARE
In 2009, the Health Information Technology for Economic and Clinical Health or HITECH Act was signed to transform the American healthcare industry. The laws worked as a forward-thinking process of changing patient services. In this regard, the Patient Protection and...
BEST PRACTICES FOR DATA PROTECTION IN THE HEALTHCARE INDUSTRIES
In the healthcare sector, safeguarding sensitive information about patients is extremely important. Patient data includes personal details, medical histories, and treatment plans. Therefore, it must be protected and should be confidential. Thus, breaches not only...
HIPAA CONSULTANTS: WE KNOW HOW TO SECURE YOUR INFORMATION
Navigating HIPAA compliance can be complex; therefore, organizations seek advice from HIPAA consultants. These HIPAA experts have specific knowledge. They can help firms to understand the problematic standards of the Healthcare Privacy Act. In 1996, HIPAA was created....




