Organizations frequently collaborate with third-party vendors to outsource critical services and functions. As data security and regulatory compliance become paramount concerns, businesses must meticulously evaluate the security practices of these vendors. One essential tool for this evaluation is the SOC report.
A vendor’s independent auditor’s thorough report, known as the Service Organization Control Report, offers information on the vendor’s internal controls over data security, availability, processing integrity, confidentiality, and privacy. For businesses entrusting sensitive data and crucial services to vendors, reviewing the Service Organization Control report is an essential step in risk management and due diligence.
This article serves as a comprehensive guide on how organizations can effectively review a vendor’s SOC report. We will delve into the different types of Service Organization Control reports, the key elements to consider during the review process, and the significance of vendor compliance with industry regulations and standards. By following this guide, businesses can make informed decisions, mitigate risks, and strengthen their data security measures when partnering with vendors.
WHAT IS A SOC REPORT AND ITS TYPES?
An independent auditor’s thorough evaluation of a service organization’s internal procedures and controls is known as a Service Organization Control Report.
A SOC report is essential for businesses that entrust critical functions or sensitive data to third-party vendors. These reports offer valuable insights into the vendor’s privacy practices. By evaluating these controls, the reports assure clients that their data is handled with the highest level of care and in compliance with industry standards.
It comes in three different categories:
1. SOC 1 Report: This report focuses on controls relevant to financial reporting. It is used when the vendor’s services impact the financial statements of their clients, such as payroll processing or financial transaction processing.
2. SOC 2 Report: The controls for security, availability, processing integrity, confidentiality, and privacy are evaluated in this study. Service Organization Control 2 is more comprehensive and commonly requested by organizations that rely on vendors for data hosting, cloud services, and data processing.
3. SOC 3 Report: Similar to Service Organization Control 2 reports, SOC 3 reports are designed for public consumption and can be freely shared with stakeholders. They are often used in marketing materials and on websites to demonstrate an organization’s commitment to security and privacy practices.
Each type of Service organization Control report serves a specific purpose and helps businesses make informed decisions when selecting vendors, ensuring the protection of sensitive data and critical services entrusted to third-party service providers.
UNDERSTANDING A VENDOR’S SOC REPORT AND ITS BENEFITS
A vendor’s SOC report is a comprehensive document that provides valuable insights into the vendor’s internal controls and processes. It is a crucial tool for enterprises to evaluate the vendor’s ability to safeguard sensitive data and ensure compliance with laws and regulations. An unbiased auditor frequently creates it.
The Service organization control report is essential for businesses that rely on third-party vendors to outsource critical functions or handle sensitive information. It offers an objective assessment of the vendor’s control environment, giving clients confidence in the security and integrity of their services.
When reviewing a vendor’s Service organization control report, businesses can gain several benefits, which are mentioned below:
1. Data Security Assessment: The Service organization control report allows businesses to assess the vendor’s data security measures, including access controls, encryption methods, and incident response protocols.
2. Compliance Verification: The Service organization control report verifies whether the vendor adheres to relevant industry-specific regulations and compliance requirements.
3. Risk Mitigation: By identifying potential vulnerabilities and weaknesses in the vendor’s control environment, businesses can proactively address risks and minimize the likelihood of security breaches or data incidents.
4. Contractual Requirements: Many businesses mandate service organization control reports as part of contractual requirements with vendors. Having Access to the report ensures that vendors are held accountable for maintaining adequate security and compliance standards.
5. Continuous Improvement: Vendors who regularly undergo Service organization control audits show their dedication to continuous improvement. Clients can monitor the vendor’s efforts to address any identified gaps and improve their control environment over time.
In conclusion, a vendor’s Service organization control report is a valuable tool for businesses to evaluate the security and compliance practices of their third-party service providers. By reviewing Service organization control reports, businesses can assess data security, verify regulatory compliance, mitigate risks, make informed vendor selection decisions, build trust, and ensure a reliable and secure partnership with vendors.

HOW DO YOU REVIEW YOUR VENDOR’S SOC REPORT?
To fully comprehend the report and its consequences for your organization, the review process entails a systematic approach.
Some steps to identify the vendor’s service organization control report effectively are:
- Review the Scope and objectives: The first step involves carefully reading the introductory sections of the SOC report to understand its scope and objectives.
- Assess the Auditor’s Opinion: An overall evaluation of the vendor’s controls will be provided in the section that details the auditor’s opinion. Any qualifications, exceptions, or shortcomings identified by the auditor must be taken into account.
- Evaluate Control Descriptions: It is critical to evaluate if the vendor’s measures comply with the security and compliance standards of your firm.
- Validate Control Effectiveness: SOC 2 Type II reports evaluate the controls’ operational efficacy. When evaluating this kind of report, look for data to back up the vendor’s statements regarding the effectiveness of the controls, such as testing methods and results.
- Analyze Complementary user entity controls: Complementary user entity controls (CUECs) are frequently referred to in SOC 2 reports. Some suppliers anticipate that their clients will already have these controls in place to support their own.
- Evaluate Monitoring and incident response: To assess a vendor’s security, it is essential to look over their monitoring, incident response, and security event management procedures.
- Seek clarification and additional information: Contact the vendor or the auditor that created the SOC 2 report if you have any questions about any portion of the report.
- Evaluate Consistency with Your Organization’s Controls: Analyze whether the outcomes outlined in the vendor’s SOC 2 report are consistent with your company’s established benchmarks for security and risk management.
- Take actions on the basis of Audit reports:Audit reports can be classified as unqualified, qualified, or unfavorable.
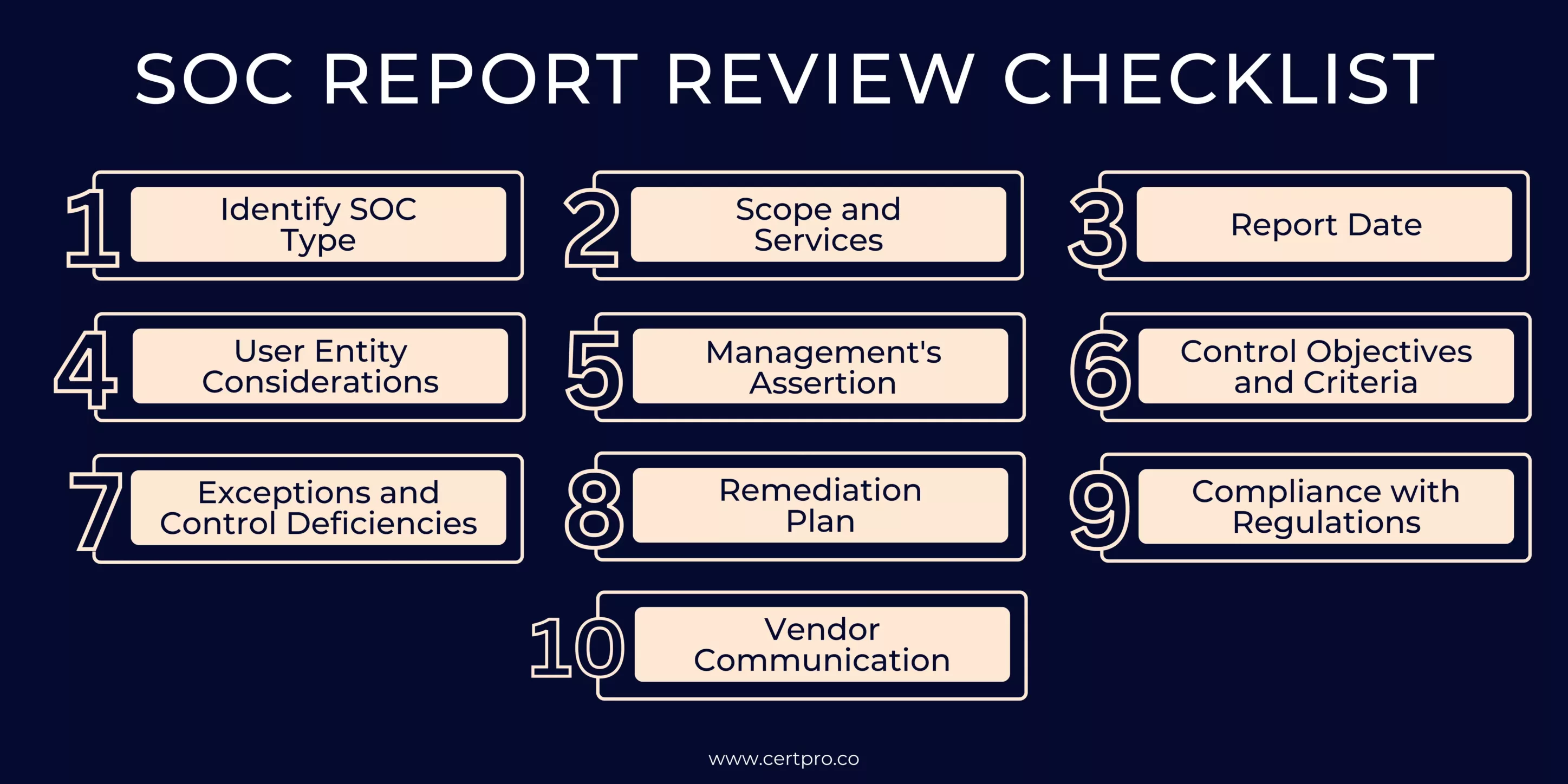
SOC REPORT REVIEW CHECKLIST
A SOC report review checklist is a valuable tool to systematically evaluate a vendor’s service organization control report and ensure that all critical areas are thoroughly assessed. Conducting a comprehensive review of the report is essential to understanding the vendor’s internal controls and their effectiveness in safeguarding data reliability, clarity, and privacy.
Here’s a detailed SOC report review checklist:
- Identify SOC Type: Determine the type of SOC report (SOC 1, SOC 2, or SOC 3) provided by the vendor.
- Scope and Services: Understand the scope of the audit and ensure it covers the relevant services provided to your organization.
- Report Date: Verify that the report is recent and covers the appropriate period.
- User Entity Considerations: Check if there are any specific considerations or limitations that apply to your organization’s use of the report.
- Management’s Assertion: Evaluate the vendor’s management assertion regarding the accuracy and completeness of the report.
- Control Objectives and Criteria: Assess whether the control objectives and criteria align with your organization’s needs and requirements.
- Exceptions and Control Deficiencies: Identify any exceptions or control deficiencies reported and assess their significance and impact.
- Remediation Plan: Review the vendor’s plan for addressing any control deficiencies and assess its effectiveness.
- Compliance with Regulations: Verify if the vendor’s controls comply with relevant regulations and industry standards.
- Vendor Communication: Engage in communication with the vendor to seek clarifications or further information on any areas of concern.
By utilizing this Service organization control report review checklist, your organization can conduct a comprehensive evaluation of the vendor’s controls, identify potential risks, and make informed decisions when engaging with third-party service providers. It ensures that the vendor’s Service organization control report is a reliable tool for assessing data security and compliance, enhancing trust in the vendor-client relationship.
STRENGTHENING VENDOR COMPREHENSIVE SOC REPORT REVIEW
Reviewing a vendor’s Service organization control report is an indispensable process that empowers organizations to make well-informed decisions when it comes to data security and compliance. A thorough and diligent Service organization control report review enables businesses to assess the vendor’s ability to safeguard critical functions and sensitive data. By scrutinizing control objectives, security measures, privacy practices, and incident response capabilities, organizations can identify potential risks and compliance gaps. Engaging in independent validation adds further credibility to the assessment. Armed with these insights, businesses can establish resilient and trustworthy vendor partnerships, ensuring the highest standards of data protection. Implementing the outlined steps and ongoing monitoring processes strengthens the vendor relationship and fosters a culture of data protection and risk mitigation.
FAQ
WHAT IS A SOC REPORT?
It is an assessment of a service provider’s internal controls for data security, availability, processing integrity, confidentiality, and privacy by an impartial auditor.
WHY IS REVIEWING A VENDOR’S SERVICE ORGANIZATION CONTROL IMPORTANT?
Reviewing a vendor’s Service organization control report is crucial for assessing their ability to protect sensitive data and comply with industry standards.
WHAT ARE THE TYPES OF SERVICE ORGANIZATION CONTROL?
It comes in three types: SOC 1 focuses on financial reporting controls; SOC 2 evaluates security, availability, processing integrity, confidentiality, and privacy controls; and SOC 3 is designed for general use and can be shared with a wider audience.
WHAT BENEFITS CAN I GAIN FROM REVIEWING A SERVICE ORGANIZATIONAL CONTROL REPORT?
Reviewing a Service organization control report allows organizations to assess data security, verify compliance, mitigate risks, and build trust in vendor relationships. It helps uphold data protection and regulatory compliance standards.
WHAT BENEFITS DO SOC 2 CONTROLS OFFER?

About the Author
SHREYAS SHASTHA DRUPADHA
Shreyas Shastha Drupadha, a Senior Business Consultant. Serving as an ISO 27001 Lead Auditor, Shreyas ensures the establishment of robust information security management systems. His expertise also encompasses GDPR, HIPAA, CCPA, and PIPEDA implementation.
HOW CAN STARTUPS ATTAIN SOC 2 COMPLIANCE IN 2024?
Trust is crucial for startups to do well in today's digital world. It's vital for establishing credibility with clients, especially in a data-driven environment where privacy is the main component. Therefore, getting a SOC 2 compliance report is crucial to building...
SOC TOOLS: How They Impact On Security Aspect Of The Organization
The changing cybersecurity landscape increases the importance of Security Operations Center (SOC) tools. Hence, it is essential for strengthening digital defenses and protecting against cyberattacks. SOC tools help security teams detect, monitor, and prevent security...
WHAT IS SOC FOR CYBERSECURITY?
In today's fast-paced digital landscape, ensuring robust cybersecurity measures is imperative for organizations aiming to protect sensitive data and maintain stakeholder trust. The American Institute of CPAs (AICPA) crafted the SOC for cybersecurity reporting...




