Data breaches and theft have become more common in today’s networked digital world, posing serious risks to companies. A lot of businesses rely a lot on working with other organizations, whether it’s sharing private documents with customers or providing reports to stakeholders. But protecting such shared data might seem like a difficult task, particularly when companies are unsure of the best ways to stop leaks.
Businesses must have thorough data breach prevention procedures in order to address this issue. This means that data must be encrypted, strict access restrictions must be put in place to restrict who can view or alter sensitive information, and monitoring systems that can quickly identify and block unwanted access attempts must be put in place. Organizations can successfully reduce the risks associated with data leaks by prioritizing data security procedures. This will protect sensitive and valuable data against breaches and unauthorized disclosures. This proactive strategy not only safeguards the company’s interests but also builds stakeholders’, partners’, and clients’ faith in the company’s dedication to data security and privacy.
WHAT IS A DATA BREACH?
When private, sensitive, or secret information is uninvited into an unprotected setting, it’s called a data breach. Unintentional or intentional attacks can lead to these kinds of breaches.
Every year, data breaches affecting millions of people stem from various incidents, such as a doctor mistakenly accessing the wrong patient’s records and extensive attempts to breach government systems for sensitive information. Given how frequently sensitive data is transmitted over the Internet, data breaches represent a serious security concern. Attackers can target practically any individual or business for breaches because of the continuous data flow. Cyberattacks often target the computers that house data stored in digital formats, which businesses worldwide utilize.
WHAT IS A PRIVACY BREACH?
A privacy breach occurs when there is unauthorized access to information due to a breach in the security of a protected computer network. Data theft or disclosure is the outcome of an intrusion. This compromised material frequently contains personally identifiable information (PII), such as names, addresses, credit card numbers, and Social Security numbers. Among other grave risks to people’s personal information, financial fraud or identity theft might result from a privacy breach. It highlights how important it is to have robust security measures in place to safeguard sensitive data and how stringent regulations must be followed to prevent unauthorized access to private information. To stop privacy invasions, a proactive approach is required. This involves implementing encryption, carrying out regular security audits, and educating staff members about cybersecurity concerns.
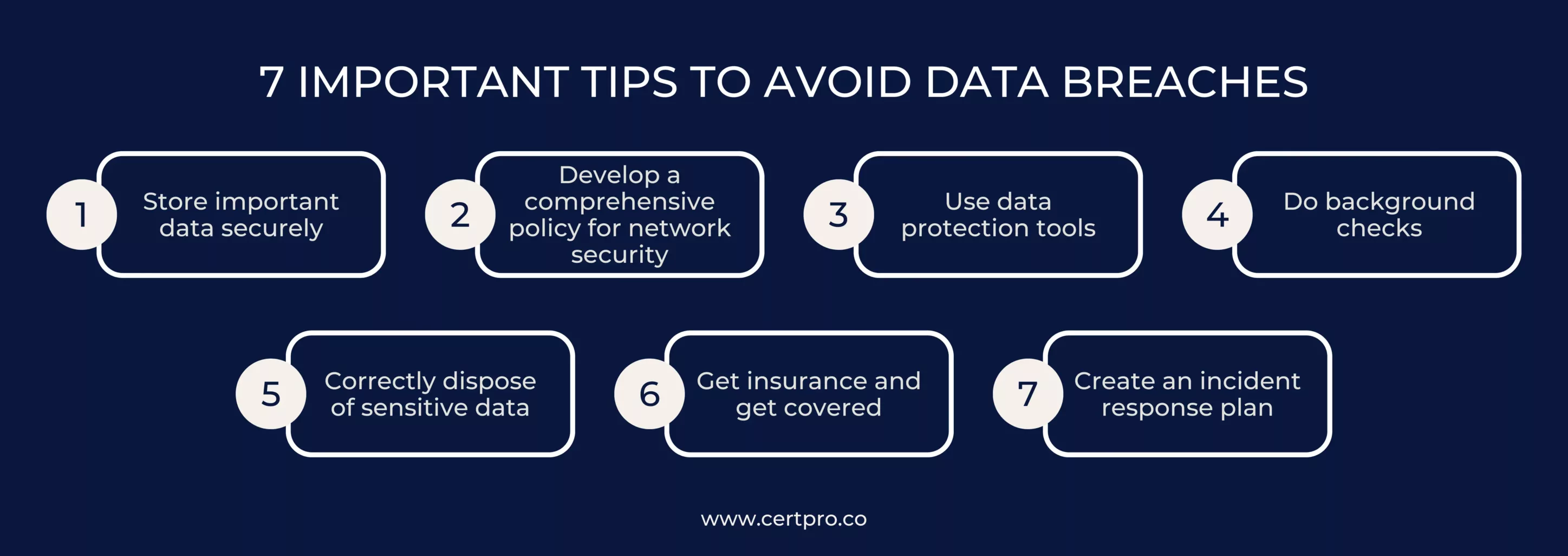
7 IMPORTANT TIPS TO AVOID DATA BREACHES
1. Store important data securely: It’s recommended to keep paper files and removable storage devices, including CDs and thumb drives, in a lockable cabinet, drawer, or safe to improve data protection. This physical storage configuration guarantees that all digital and physically sensitive materials are protected from unwanted access. Only those with a genuine need for the information kept there should be able to access these secure storage spaces. Organizations can lessen the risk of data breaches and unauthorized disclosures by restricting access to only authorized individuals. In order to safeguard private standards within the company and safeguard sensitive data, a complete plan that includes proactive physical security measures is formed.
2. Develop a comprehensive policy for network security: A network security policy should include a number of important components. First, make sure that everyone who works for the company—owners, partners, and employees—is aware of the data assets and sharing permissions. For network access, specify that passwords must be changed on a regular basis. Passwords must not be kept in digital or handwritten files. Define precise requirements for remote network access in order to preserve data transfer protocols and secure connections. Remind staff members of policy details on a frequent basis to avoid unintentional data privacy violations. Organizations can reduce the risk of illegal access and data breaches and improve network security by putting these precautions into place. This proactive approach to network security complements physical security measures, resulting in a comprehensive plan to protect proprietary standards and sensitive data inside the company.
3. Use data protection tools: It’s critical to understand that cybercriminals are skilled at taking advantage of weaknesses in systems. To protect data while it is being transmitted and kept on computers, encryption software must be installed and tested on a regular basis. Installing a firewall is also necessary to stop illegal access to your network from the Internet. Solutions might vary from low-cost options to more expensive ones that cost thousands of dollars, depending on how sensitive your data is. Setting these security precautions as a top priority will help to reduce the likelihood of data breaches and guarantee that private data is safe from online attacks.
4. Do background checks: Employees, vendors, and contractors are among the most common causes of privacy data breaches. Background checks on those who need access to secret information are critical. It is critical to establish user levels and assign appropriate access across the network. For example, ordinary operations such as checking emails should be performed using a secondary account with limited permissions, separate from the one used to access personal data. Implementing these procedures can help firms reduce the likelihood of privacy breaches and improve the security of sensitive information.
5. Correctly dispose of sensitive data: It is not recommended to simply recycle or reuse documents and equipment without taking security precautions. Shredded papers holding private information should be discarded, and information should be removed from devices. Even though it can seem apparent, incorrectly erasing data from computers and storage devices is a frequent error. This error presents an opportunity for hackers to recover data they thought had been deleted. Consequently, in order to guarantee the total removal of sensitive data and reduce the possibility of unauthorized access or data breaches, it is imperative to adhere to appropriate data disposal processes.
6. Get insurance and get covered: Even with all the precautions described above, data privacy breaches can still happen to you. Hire a third party to create an insurance plan that will protect you against the costs related to cyber liability. This extra layer of security gives you peace of mind and strengthens the security measures already in place at your company by assisting in reducing the financial risks connected with future data breaches.
7. Create an incident response plan: Information on how to store and back up sensitive data, as well as who can access it, should all be included in an incident response strategy. A list of contacts for prompt notice, such as legal practices, credit monitoring services, forensic data specialists, and public relations businesses, should also be included. A prompt reaction to an attack is essential for both quick recovery and damage reduction. A breach of data privacy can significantly interrupt corporate operations and result in large recovery costs. Businesses can drastically reduce the risk of data privacy breaches and the repercussions that follow by putting the suggested procedures into practice.
WHAT CAUSES DATA LEAKAGE?
1. Physical actions: While it is commonly considered that hackers primarily use remote hacking methods, they frequently use physical flaws to obtain access to data. This includes the theft of physical objects such as documents, laptops, phones, and storage devices. Furthermore, they may gain unauthorized access to physical assets and make copies without being detected. This emphasizes the significance of not only safeguarding digital networks but also having strong physical security measures to prevent illegal access. Surveillance cameras, access control systems, and employee training in detecting and reporting suspicious activity are examples of such methods. By addressing both digital and physical security threats, organizations can effectively reduce the threat posed by cybercriminals attempting to obtain unauthorized access to critical data.
2. Social engineering: Protecting your company from internet security risks is critical to an efficient data breach prevention plan. You’re probably acquainted with phishing, a method in which fraudsters create fraudulent emails that resemble legitimate correspondence in order to deceive recipients into disclosing critical information.
For example, they could create a fake email pretending to be your company’s IT department and ask for a staff member’s password to be reset in order to access their accounts without authorization. Scammers can get sensitive information through these phone calls or email scams, which they then either use for fraudulent activities or sell on the black market. It’s essential for organizations to educate employees about identifying phishing attempts, employ email filtering systems to flag suspicious messages, and implement multi-factor authentication to fortify defenses against such malicious tactics. Businesses can reduce their exposure to phishing attempts and prevent unauthorized access to sensitive data by being alert and taking proactive security steps.
3. Human error: Not every data leak results from malevolent intent. Approximately 52% of breaches, according to IBM, are the consequence of intentional attacks. Accidents are another important factor in which people unintentionally handle private information improperly. This can entail transmitting data to the incorrect destination or leaving it exposed in unsafe places. Human error continues to be a major contributing element in data breaches, even with strict security measures in place. Thus, in addition to putting strong cybersecurity measures in place, companies also need to give top priority to extensive employee training programs that encourage understanding and compliance with data security guidelines. Businesses may reduce the risk of deliberate assaults and unintentional breaches by cultivating a culture of accountability and awareness. This will protect sensitive data and preserve stakeholder trust.
DATA BREACH BEST PRACTICES
Data breach prevention is crucial since it can have serious financial repercussions. It is imperative to invest capital in order to implement robust data security procedures. As a worker or small business owner, you may greatly lower the chance of security breaches by implementing these best practices for data breaches. You maintain stakeholder and customer trust while protecting sensitive data by doing this.
1. Train your workers: One of the most important tactics for stopping data breaches is to combat ignorance. It is essential to train staff members on data protection procedures. This includes instructing them on how to create secure passwords, offering guidance on changing passwords on a regular basis, and teaching them to spot and report phishing scams and other questionable activity. Employees are empowered to actively participate in protecting sensitive data by taking preventive data security measures.
2. Establish and maintain processes: To create a clear expectation inside your organization, data security processes must be established and updated on a regular basis. By doing this, you encourage staff members to prioritize data protection by demonstrating your commitment to it. By providing the right degrees of access, roles, and permissions for sensitive data access, like those found in PaySimple, we improve security. This preventive action fortifies compliance with data protocols and protects your company.
3. Data backup and recovery: Regular backups are essential since data breaches can lead to the malicious erasure of all data. Having data backed up ensures fast recovery in the event of loss, server failure, or natural calamities. Your IT staff can ensure constant protection against data loss, preservation of important information, and business continuity by putting automated offsite backup systems in place.
4. Keep only what you need: Perform routine audits and streamline computerized data storage, eliminating superfluous information. Combine the storage of private information in one area while keeping detailed records of its movements. Follow company or industry guidelines for data retention, keeping records for certain amounts of time. By taking a proactive stance, data security is improved and regulatory compliance is guaranteed.
5. Protect physical data: Data breaches can result from physical actions; hence, it is imperative to safeguard all data, including physical files. Only necessary personnel should be able to access physical records that are safely stored in authorized areas. Securing sensitive data physically lowers the possibility of unwanted access and strengthens data security protocols overall.
6. Empower workers with best practices: Workers using work computers need to understand the risks associated with specific websites, such as file-sharing services. This understanding should include how they use their mobile devices for work. Stress how important it is to keep business-related activity on work computers and use personal devices for personal tasks, especially in remote work circumstances. This isolation reduces the exposure of work devices to potential security risks.
7. Maintain up-to-date security software: Strong security protocols must be in place in order to stop breaches. Purchase security software, then set up automated scans on a regular basis. Software that blocks viruses, malware, and firewalls is essential for preventing data breaches. Work with an internet security team or supplier to efficiently configure and optimize these solutions, strengthening the defenses of your company against cyberattacks.
8. Data encryption: Give encryption top priority when emailing sensitive information. Create a specific, private network for Wi-Fi networks that is closed to the general public. If processing really sensitive data over Wi-Fi is something you want to consider banning to avoid prospective thieves intercepting your information. These safety data security measures improve data security by reducing the hazards connected to email and Wi-Fi transmission.
9. Protect portable devices: Secure portable devices like flash drives, cell phones, and tablets with strong, hard-to-guess passwords to reduce the chance of loss or theft. Put in place extra security measures and anti-theft software to limit access to only authorized people. These safety measures improve defenses against unwanted access and secure private information kept on portable devices.
10. Hire an expert: It’s hard to run a small firm, and you might not be good at focusing on data breaches. To manage this part, think about hiring a security specialist or asking for guidance on best practices. Working with suppliers who offer all-inclusive security solutions can help reduce the workload as well. For example, PaySimple uses top-notch PCI-compliant security methods to securely store consumer and financial data, reducing risk for your company and guaranteeing client protection.
FAQ
How can I ensure that my company's data protection measures are up-to-date with evolving cyber threats?
To ensure your company’s data protection measures are up-to-date with evolving cyber threats, regularly assess your security posture, stay informed about emerging threats, update software and systems promptly, and invest in ongoing employee training and awareness programs.
What steps can I take to effectively train my employees in data security protocols and awareness?
Effective training in data security protocols and awareness involves conducting regular workshops, providing resources such as guidelines and best practices documents, simulating phishing attacks for hands-on learning, and encouraging a culture of accountability where employees feel empowered to report suspicious activity.
Are there any specific regulations or compliance standards I need to adhere to in order to prevent data breaches?
Depending on your industry and location, you may need to comply with regulations such as GDPR, HIPAA, or PCI DSS. Stay informed about relevant laws and standards, conduct regular audits to ensure compliance, and seek legal guidance if needed to ensure your data protection measures align with regulatory requirements.
Do cybercriminals target small businesses for data breaches?
Yes. Cybercriminals often target small businesses due to their perceived lack of robust security measures. It’s crucial for small businesses to prioritize cybersecurity to protect sensitive data.

About the Author
RAGHURAM S
Raghuram S, Regional Manager in the United Kingdom, is a technical consulting expert with a focus on compliance and auditing. His profound understanding of technical landscapes contributes to innovative solutions that meet international standards.
HOW DOES THE NIST CYBERSECURITY FRAMEWORK FUNCTION, AND WHY IS IT IMPORTANT?
Emerging cyber threats make cybersecurity an essential consideration for organizations handling and managing data. In this regard, the NIST cybersecurity framework applies to improving your cybersecurity program. It is a set of guidelines that helps improve your...
UNDERSTANDING ISO 42001: A GUIDE FOR RESPONSIBLE AI MANAGEMENT SYSTEMS
The invention of artificial intelligence (AI) has changed the operational processes of many industries. However, the rapid growth of technology increases ethical, security, and privacy-related concerns. Therefore, the International Organization for Standardization...
EUROPEAN UNION’S ARTIFICIAL INTELLIGENCE ACT: HOW THIS GROUNDBREAKING LAW AFFECTS YOUR BUSINESS
Nowadays, Artificial Intelligence (AI) is transforming our lives exceptionally well. AI is now streamlining healthcare services, providing virtual assistance, and fulfilling queries. Technologies have boons and curses. Similarly, AI creates many concerns about...




