Emerging cyber threats make cybersecurity an essential consideration for organizations handling and managing data. In this regard, the NIST cybersecurity framework applies to improving your cybersecurity program. It is a set of guidelines that helps improve your organization’s cyber security posture. In addition, the framework provides a set of recommendations and standards related to potential threat identification. Furthermore, the guidelines help mitigate risk and prevent cyber incidents.
If you want to know more about the NIST framework and how it functions, then read the article. The article will detail how the NIST framework functions and why it is essential for your organization. In addition, the article will discuss the process of incorporating the framework in your workplace.
NIST CYBERSECURITY FRAMEWORK
The National Institute of Standards and Technology is a non-regulatory agency that promotes innovation by advancing measurement. Furthermore, the framework recognizes an organization’s cybersecurity weaknesses and offers a set of rules and regulations appropriate for industry standards. It is the gold standard for developing a concrete cybersecurity framework. Similarly, suppose your organization is creating a cybersecurity program or running a reasonably mature one. In that case, the NIST cybersecurity framework is an effective security management tool that helps avoid cybersecurity risks. The tool is flexible enough to integrate with an organization’s security processes. It offers an excellent starting point for implementing a robust cybersecurity framework.
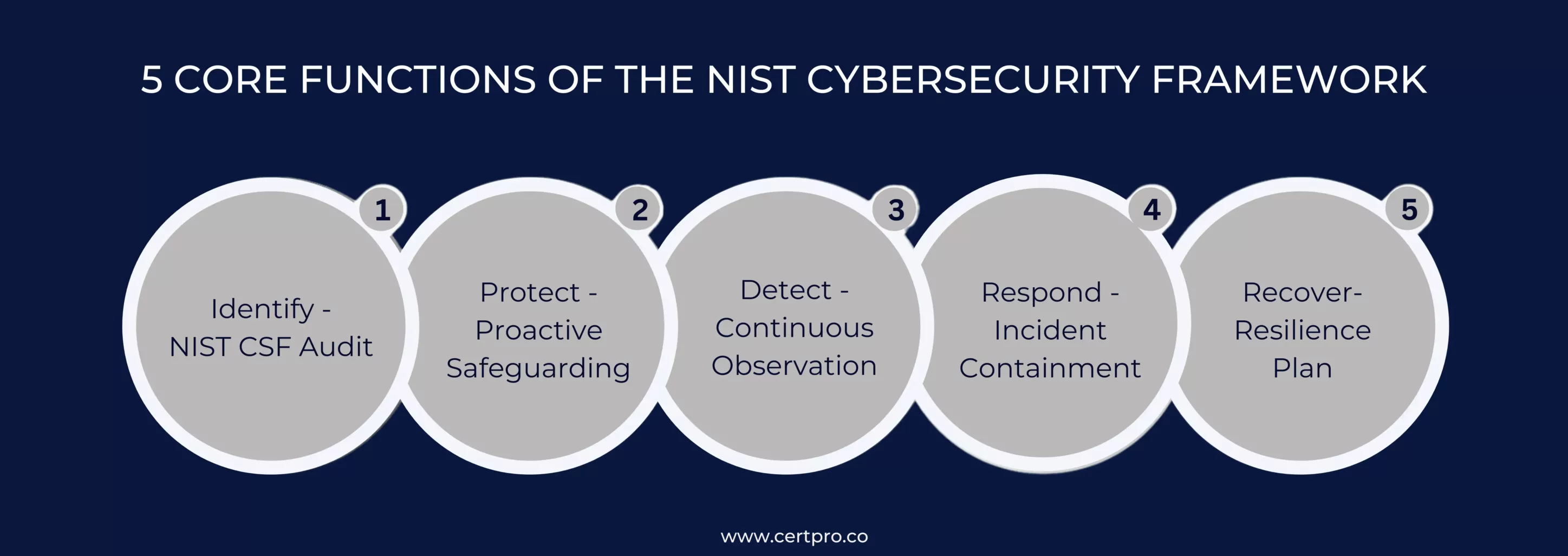
5 CORE FUNCTIONS OF THE NIST CYBERSECURITY FRAMEWORK
The NIST CSF categorizes cybersecurity activities into these 5 core functions:
Identify-NIST CSF Audit: It is focused on laying the groundwork for an effective cybersecurity program. The function emphasizes understanding the business context and resources that might cause cyber threats. Therefore, the comprehensive self-assessment enables the opportunity to understand risk management capabilities. The process assists the organization in focusing on its risk assessment strategy and business needs. In addition, it helps in asset management programs by identifying physical and software assets. The function recognizes the organization’s business environment and asset vulnerabilities. Applying the NIST cybersecurity framework creates legal and regulatory compliance governance by implementing a risk management strategy.
Protect – Proactive Safeguarding: In NIST compliance, the Protect function is defined as a proactive safeguard that ensures critical infrastructure and support to prevent the risk of potential cyber-attacks. It implements access controls and identity management programs through physical and remote access. The function empowers the employees with security training programs to create security awareness. A data security strategy must be established in these cybersecurity measures to protect information confidentiality, integrity, and availability. Furthermore, the function implements procedures to manage the information systems and assets. The framework manages the technology and ensures the security of policies and procedures.
Detect – Continuous Observation: It is crucial to identify potential cybersecurity incidents. Therefore, the function recognizes the appropriate activities to identify cybersecurity incidents. The function enables the identification of anomalies and events, along with their possible actions. In addition, it implements continuous monitoring capabilities to monitor cybersecurity events. Furthermore, continuous observation verifies the effectiveness of the measures.
Respond – Incident Containment: It focuses on taking the correct measures in case a cybersecurity incident is detected. Furthermore, the function supports the containments that may be affected by the incident. It ensures that the response planning processes are effectively executed during and after an incident. In this context, it manages communications with the stakeholders after the incidents. The most crucial function of response is to analyze the incident and develop a recovery plan according to its impact. In addition, response mitigates the risks and prevents the expansion of the incident.
Recover—Resilience Plan: This function identifies the activities to restore and maintain resilience plans. It restores the capabilities or services affected by cybersecurity threats, reducing the impact of cybersecurity incidents and helping to continue functionality. In addition, this function ensures that the organization has a robust recovery planning process to restore the affected assets. It enables internal and external communications during recovery and improves based on existing strategy reviews.
IMPORTANCE OF NIST CYBERSECURITY FRAMEWORK
Your organization might require a robust cybersecurity framework to prevent data losses in today’s data-savvy world. Unseen risks and vulnerabilities emerge regularly that risk your business. In addition, if you are not maintaining an asset inventory that requires protection or cannot determine the real impact of potential risks, then compliance with the NIST cybersecurity framework can be a wise decision for your organization. The framework helps you overcome the challenges regarding cybersecurity. The benefits of NIST compliance are discussed below:
Execute Robust Cybersecurity: The NIST cybersecurity framework is a voluntary approach recognized as an industry best practice. It is a comprehensive framework for control that prioritizes cyber threats and develops a cybersecurity strategy.
Improve Business: Incorporating cybersecurity practices in your organization enhances its selling point. Moreover, a gold cybersecurity standard fosters trust and partnership, making business growth more relevant and desirable.
Bridge the Gap: Implementing the NIST cybersecurity framework ensures better organizational communication and decision-making processes. It aids in security budget allocation and develops a common language for business goals.
Flexibility Framework: NIST CSF is the most flexible framework many industries have successfully adopted. It is highly adaptable and customizable because it is a voluntary framework. The framework develops a blueprint that offers ongoing guidance on cybersecurity.
Assure Growth: Multiple organizations and government agencies execute the framework for improving their regulations and compliance posture. This trend increases the compliance bar and ensures data safety.
IMPLEMENTING THE NIST CYBERSECURITY FRAMEWORK
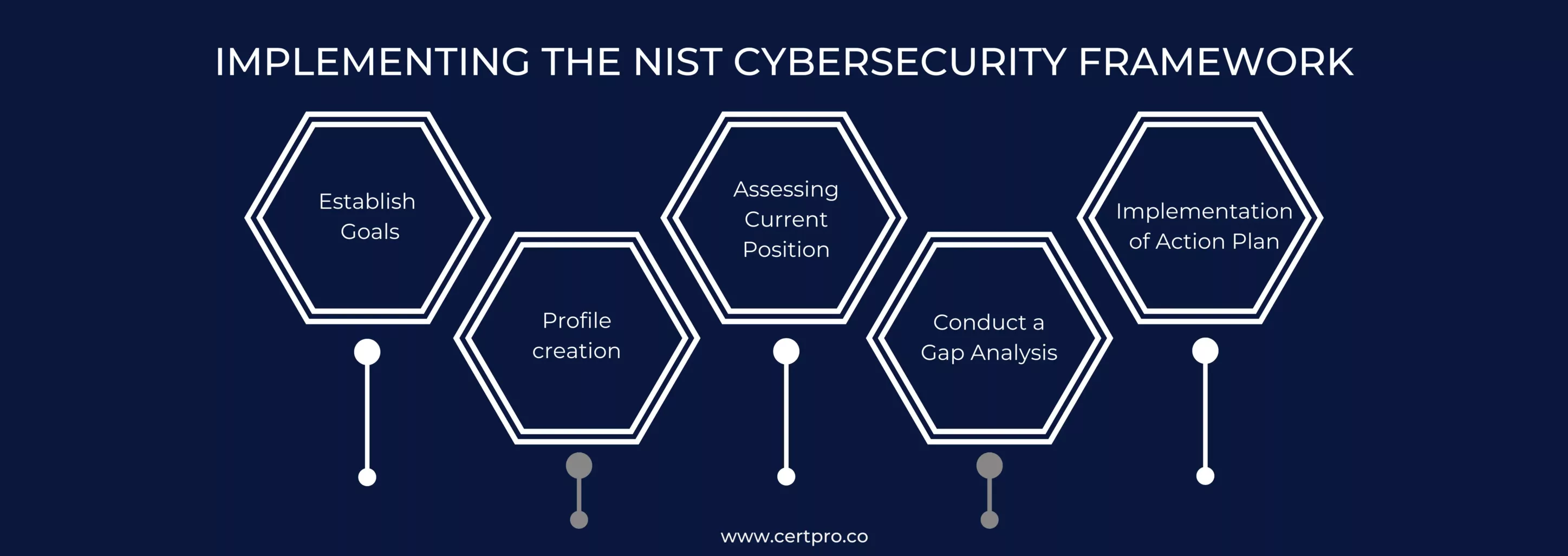
After recognizing the positive impact of the NIST cybersecurity framework on cybersecurity measures, you may wonder how to apply it to your organization. Here are the five steps to implementing a successful NIST framework for your organization.
Establish Goals: Implementing the NIST framework requires establishing a set of goals regarding data security. This helps measure the success of applications. You need to recognize the organization’s tolerance for risk and prioritize the areas that need protection. In addition, your budget consideration is essential for implementation. Therefore, establishing the goal helps develop an action plan and clear the organization’s motive regarding the NIST implementation.
Profile creation: The NIST framework is a voluntary guideline for various industries. It is tailored to each organization’s demands so that it may look different from one organization to another. Therefore, the profile outline signifies the specific needs of the organizations and tailors the framework accordingly. Thus, with the assistance of the implementation tiers, an organization’s cybersecurity can reach from Tier 1, which is reactive to cybersecurity events, to Tier 4, which is proactive in its cybersecurity controls.
Assessing Current Position: A detailed risk assessment is essential before implementing the NIST framework. Thus, it offers valuable insight into your organization’s cybersecurity practices and identifies areas for improvement. In this regard, you can utilize tools to find the security efforts or seek help from cybersecurity specialists to conduct a risk assessment.
Conduct a Gap Analysis: The organization recognizes its vulnerabilities and threats after completing an NIST audit. In addition, it helps identify gaps in cybersecurity measures. Furthermore, using the score in risk assessment emphasizes the risks that need priority and develops an action plan accordingly.
Implementation of Action Plan: The last stage is implementing the NIST CSF after considering the risk assessment and gap analysis. Again, the organization must remember that implementing the NIST audit requires continuous monitoring and improvement. Continuous governance ensures the framework’s effectiveness and customizes the measures according to business demands.
THE WAY FORWARD
Creating a strong cybersecurity strategy in the modern business landscape should be an inevitable part of business operations. Therefore, the NIST cybersecurity framework enables organizations to assess and implement a proper cybersecurity framework through its core guidance. Thus, if your organization plans to implement a cybersecurity framework, consider the NIST, as it can ensure data safety. Furthermore, the implementation process can be complex; you can seek help from an expert for better results. Thus, expert guidance and recommendations can enhance the framework’s capabilities and reduce the risk of data breaches.
FAQ
What is the NIST CSF report?
The NIST CSF Report is used for information security management. The report also helps build trust with stakeholders and develop partnerships.
Is your organization required to use the CSF?
It is a voluntary standard. However, the framework is mandatory for U.S. Federal Government agencies. In addition, some companies require CSF from their customers. Therefore, implementing the NIST CSF enables business opportunities and safe business practices for your organization.
Does the CSF provide a recommended checklist?
The CSF does not provide any checklists. It emphasizes identifying cybersecurity risks but does not specify the actions to achieve the desirable outcomes.
Does the CSF help in the cost-effectiveness of cybersecurity practice?
Yes. It reduces the cost related to cybersecurity measures, prioritizes the expenditure, and improves business growth.
What are Framework Implementation Tiers?
The framework has four tiers that describe the cybersecurity risks of organizations and how they will be managed.
Partial: Tier 1
Risk-Informed: Tier 2
Repeatable: Tier 3
Adaptive: Tier 4

About the Author
RAGHURAM S
Raghuram S, Regional Manager in the United Kingdom, is a technical consulting expert with a focus on compliance and auditing. His profound understanding of technical landscapes contributes to innovative solutions that meet international standards.
UNDERSTANDING ISO 42001: A GUIDE FOR RESPONSIBLE AI MANAGEMENT SYSTEMS
The invention of artificial intelligence (AI) has changed the operational processes of many industries. However, the rapid growth of technology increases ethical, security, and privacy-related concerns. Therefore, the International Organization for Standardization...
EUROPEAN UNION’S ARTIFICIAL INTELLIGENCE ACT: HOW THIS GROUNDBREAKING LAW AFFECTS YOUR BUSINESS
Nowadays, Artificial Intelligence (AI) is transforming our lives exceptionally well. AI is now streamlining healthcare services, providing virtual assistance, and fulfilling queries. Technologies have boons and curses. Similarly, AI creates many concerns about...
How to Implement GRC Frameworks in 2024: Step-by-Step Guide
The rapidly evolving business environment, complexity, and accountability enhance the importance of the organization's governance, risk management, and compliance initiatives. Therefore, if your company finds difficulties expanding, recheck your organization's...