The software, hardware, network connections, information security, services, and service providers of the business take these factors into account when determining the security posture of the organization. These are the components that are scrutinized primarily for a good security posture. A better Infosec posture helps you build your cybersecurity strategies for the company, ensuring the security of the information is protected, and also helps in any malware intrusions and data breaches. Your company’s security posture is very critical for its cybersecurity. This article is purely for information about security posture—what is it? How do I build one? Why is it important?
Your IT security team painstakingly created these cybersecurity measures to protect against potential security flaws, lower the risks posed by various types of malicious software and cybercriminal activity, and successfully thwart any attempts at the unauthorized acquisition of priceless intellectual property. Your company can ensure the highest level of protection for its digital infrastructure by putting these comprehensive strategies into practice, strengthening its resistance to changing cyberthreats, and fortifying the defenses that guard against potential breaches, data breaches, and the compromise of sensitive information.
WHAT IS INFOSEC POSTURE?
Information security posture is a set of guidelines for the overall state of your company or the condition of your organization’s information security defenses, capabilities, and practices. It indicates an organization’s overall security posture and readiness to protect its information assets from attacks and vulnerabilities. A company that has taken strong information security measures to safeguard its infrastructure, data, and systems is said to have a strong information security posture.
WHY IS INFORMATION SECURITY POSTURE IMPORTANT?
Information security is the top priority these days. Your company’s security posture should be a priority since it helps mitigate cybersecurity risks. A better security posture reduces cybersecurity risks. The probability of exposure or actual loss from cyberattacks, data breaches, and other cyberthreats is known as cybersecurity risk. Cybersecurity risks have the potential to kill your company’s security infrastructure or IT assets confidentiality, integrity, or availability.
Now ensuring cybersecurity and establishing the company’s data privacy is crucial. These laws, which are mentioned, are globally recognized regulations that are used to protect the data of your company and help in mitigating the risks. General Data Protection Regulation (GDPR), the Brazilian General Data Protection Law (LGPD), the Personal Information Protection and Electronic Documents Act (PIPEDA), and the California Consumer Privacy Act (CCPA). Industry-specific regulations like the Gramm-Leach-Bliley Act (GLBA), the Federal Information Security Modernization Act (FISMA), the Australian Prudential Regulation Authority’s CPS 234, the New York Department of Financial Services’ (NYDFS) Cybersecurity Regulation, and the Health Insurance Portability and Accountability Act (HIPAA) have also increased the need to prioritize cybersecurity and data privacy practices.
These are the regulations that let us know what kind of data must be protected and also help in suggesting security protocols. For example, encryption, access controls, etc. A habit of monitoring regularly and maintaining your infosec posture is better for the company and helps prevent risks. Cybercriminals are always finding their own ways to exploit even the best IT security measures.
HOW TO BUILD OR IMPROVE SECURITY POSTURE
The first step in determining your cybersecurity maturity level and cyber breach risk is to examine your security posture. You should be able to respond to the following inquiries:
1. How secure is the organization?
2. Do we have the right cybersecurity strategy?
3. How good are our security controls?
4. Can we quantify cyber resilience and breach risk with accuracy?
5. How can the various risk owners in the company be scored and compared?
Information security posture has been mentioned as a very important element in protecting data and mitigating cybersecurity risks. Applying a security posture to your company is a strenuous process. But by using this seven-step method, it can be very helpful for companies to learn the process of creating one or improving an existing one.
The seven-step method:
1. Performing a cybersecurity risk assessment: Start by carefully evaluating the present security posture of your company. This assessment helps you know what problems your company is facing. Determine any possible gaps, dangers, or vulnerabilities in the systems, networks, apps, and data storage components of your digital infrastructure. It also helps you determine what actions should be taken to eliminate any particular risks.
Note: While conducting the assessment, also check with the third-party vendors of your company so you can identify and mention any vulnerabilities they may have in their systems.
2. Developing a clear security strategy: When a breach is discovered, a security management strategy will specify what to do next and speed up future remediation efforts. Knowing which teams will handle certain tasks will promote collaboration and enhance communication. Setting benchmarks for your incident management plan’s efficacy through the execution of a test breach can help it become stronger and more effective over time.
3. Prioritize the risks by their impact on the business: The following stages include patching and remediating after you’ve identified the risks and vulnerabilities you are experiencing. We can save time and money by prioritizing the risks that occur in business-critical applications. It will be easier to take corrective action, manage time and resources, and manage risks after a method for risk assessment has been devised.
4. Strengthen access controls: By implementing them to guarantee that only authorized users have access to critical resources. Use robust authentication techniques, such as multi-factor authentication, and uphold the least privilege principle by giving users just the access privileges they need to fulfill their tasks.
5. Break down the silo rule: Siloed IT teams inside organizations frequently suffer from poor communication, which can raise the likelihood of unfavorable consequences in the case of a threat. Technologists can better understand how each team is impacted before, during, and after a breach by fostering a collaborative culture.
6. Build an automated system to reduce errors and threats: It is practically impossible for administrators to remain on top of all potential dangers within current apps. Therefore, depending only on the administrator exposes users to a high risk of human error due to inevitable security holes in the software.
7. Regular checks and updates: Maintain the most recent security patches and upgrades on all programs, operating systems, and apps. Apply patches often to fix known issues and reduce the chance that they may be exploited.

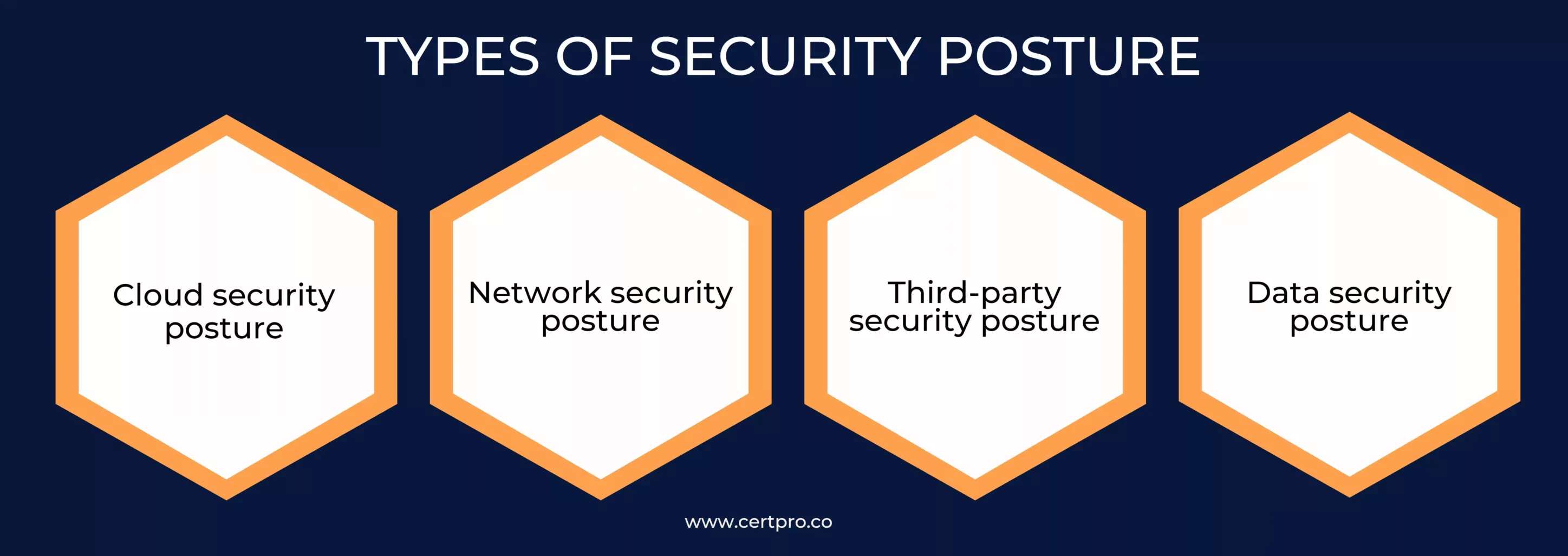
TYPES OF SECURITY POSTURE
We all now know how important a security posture is, but knowing more about these pictures will make us understand that there are more types of security postures than one. Now we will get to know the types of security postures.
- Cloud security posture: The overall security standing and preparedness of a company’s cloud computing infrastructure are referred to as cloud security posture. It includes all of the safeguards, procedures, and policies implemented to safeguard information, software, hardware, infrastructure, and other resources used in cloud deployments. The organization’s cloud-based assets are appropriately secured from possible attacks and vulnerabilities thanks to a solid cloud security posture.
- Network security posture: The state of an organization’s computer network’s overall security and preparedness is referred to as its “network security posture.” It includes all of the safeguards, settings, and procedures put in place to guard against unauthorized access, threats, and vulnerabilities to the hardware, software, and data that make up the network infrastructure. The organization’s network is well-defended and robust against possible attacks when it has a strong network security posture.
- Third-party security posture: Third-party security posture is the review and assessment of the security policies and preparedness of other organizations, such as suppliers, vendors, or service providers, with whom an organization shares sensitive information or depends for vital business operations. In order to ensure the safety of the data, systems, and assets entrusted to them, it requires evaluating the security measures, controls, and policies adopted by third parties.It is crucial to evaluate the security posture of an organization’s external partners because their security policies can have an impact on the security of its data and resources. The ecosystem of the company may become vulnerable due to a third party’s lax security posture.
- Data security posture: The general state or condition of an organization’s data protection procedures, capabilities, and measures is referred to as its data security posture. It includes all of the measures taken to guarantee the confidentiality, availability, and integrity of sensitive data throughout its lifespan. A company with a strong data security posture has taken the necessary precautions to guard against unwanted access, loss, or change of its data.
FAQ
Whose awareness is security posture targeted toward?
The audience for the evaluation is top management and C-Level executives. Your firm will be able to comprehend the return on investment (ROI) of security because it gives crucial knowledge on potential locations where cybersecurity expenses and resources will be required.
What makes an effective cybersecurity posture at its core?
The eight components of an effective cybersecurity posture are:
- Asset Management and Identification
- Risk Control
- Access Control
- Threat Control
- Security measures
- Recovery from disasters and business continuity
- Management of incidents
- Security awareness, education, and training
How can you tell if a business has established proper security posture?
Assessments of security posture are based on the following presumptions:
- Companies need to understand the value of the data they have and the safeguards they have in place.
- Businesses ought to be able to assess their situation.
- Organizations must understand what they must accomplish and the path they must take to get there.
How can organizations assess their information security posture?
Organizations can assess their security posture through various means, such as conducting regular risk assessments, vulnerability assessments, penetration testing, security audits, and evaluating their compliance with relevant security frameworks or standards.
What are some typical risks that businesses need to be aware of? Typical dangers include:
- Social engineering schemes and phishing assaults
- Viruses and ransomware infestations are examples of malware.
- Employee negligence or wrongdoing; Insider threats
- assaults that use distributed denial of service (DDoS).
- Unauthorized access and data breaches
- APTs, or advanced persistent threats
- vulnerabilities in web applications.

About the Author
SUBBAIAH KU
Subbaiah Ku is the Regional Director for CertPro in Oman, bringing a wealth of expertise in process and system auditing. As a seasoned lead assessor, Subbaiah is dedicated to ensuring the highest standards in compliance and security. His unique blend of technical acumen, rooted in Mechanical Engineering, is complemented by a diverse range of certifications and extensive training.
AI SECURITY: UNDERSTANDING THREATS AND COMPLIANCE SOLUTIONS
Artificial Intelligence continues to grow and become more relevant in workplaces. Customers widely use it to handle and market products. Organizations are desperately using AI for their businesses and ensuring that the AI systems comply with the new rules and...
HOW DOES THE NIST CYBERSECURITY FRAMEWORK FUNCTION, AND WHY IS IT IMPORTANT?
Emerging cyber threats make cybersecurity an essential consideration for organizations handling and managing data. In this regard, the NIST cybersecurity framework applies to improving your cybersecurity program. It is a set of guidelines that helps improve your...
UNDERSTANDING ISO 42001: A GUIDE FOR RESPONSIBLE AI MANAGEMENT SYSTEMS
The invention of artificial intelligence (AI) has changed the operational processes of many industries. However, the rapid growth of technology increases ethical, security, and privacy-related concerns. Therefore, the International Organization for Standardization...




